tuff checker
Solved by : grb
This is what the challenge looks like, there's a binary file attached with it.

As always, we're going to open the attached binary under IDA. This is the function that will greet us. There's also a global variable called aura and a flag function that will print our flag.
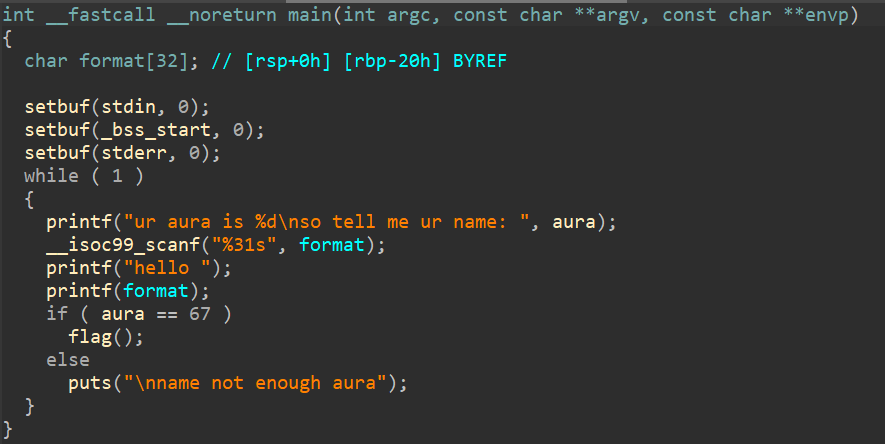
So, our objective here is to somehow overwrite the global variable aura with 67. But how can we do that? Well, as you can see, the main function takes input and then pass it directly to printf, which leads to a potential format string attack. We need to do an arbitrary write using format string attack. Using format string, we can do an arbitrary write using the %n format string, how it works is that it will write how many the printf have been written to the stdout until that %n format is found. So, for example, a AAAAA%n format string will write the value 5 to the pointer thats passed to the printf function.
Before crafting our exploit, lets do some background check on the binary, as usual, we check the security mitigiations on the binary using checksec.
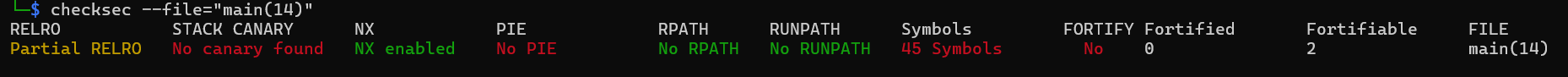
Very nice, next, for the %n format string to write to our target address, we need to locate where our format buffer is in the stack, we can do this easily by passing something like this AAAA.%p.%p.%p.%p.%p.%p.%p.%p.%p.

So, as we can see here, the format buffer sits at offset 6, next, lets locate where does the variable aura is at.
Nice, lastly, lets craft our exploit with the help of pwntools. You can check it out here. And when we run it...

PO- PO- PO- PWNED!!!
Here, you can see that our exploit looks like this
b'%67c%8$llnaaaaba\x8c@@\x00\x00\x00\x00\x00'
the %67c part is make printf print 67 characters, which will be our value, the %8$lln part is our arbitrary write format, the aaaaba part is our padding so that our payload is 8 bytes aligned, and the rest is our target address. You might ask, "Hey grb, why %8$lln and not %6$lln?", well if its %6$lln, then the printf will read the %67c%8$l part of the payload, if its %7$lln, the printf will read the lnaaaaba part, and if its %8$lln, the printf will read our address part, which is \x8c@@\x00\x00\x00\x00\x00 or \x8c\x40\x40\x00\x00\x00\x00\x00.