ICMP
Solved by : grb
aku ngirim rahasia ke google
author: hyall
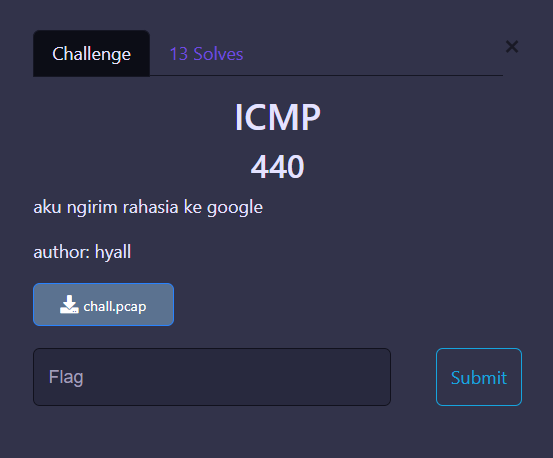
It's clearly visible in the provided pcap file that all of these are ICMP requests, and based on the clue, we can determine we are looking for requests directed to 8.8.8.8. We can also see that the data within those files contains one character representing a letter in the flag.
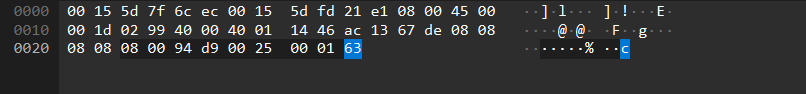
Let's extract using the payload:
$lines = tshark -r rodac.pcap -Y 'icmp and ip.src==172.19.103.222 and icmp.type==8' -T fields -e frame.number -e data.data; $hex = ($lines | Sort-Object { [int]($_ -split "`t")[0] } | ForEach-Object { ($_ -split "`t")[1] -replace '[:\s]','' }) -join ''; $bytes = for ($i=0; $i -lt $hex.Length; $i+=2) { [Convert]::ToByte($hex.Substring($i,2),16) }; [System.Text.Encoding]::ASCII.GetString($bytes) -replace "\r?\n",""
compit{HOLY_SHEEEET_YOU_CAN_FIND_ME!!!!}
You ate that!👍👍👍