flag PDF
Solved by: grb
This is what the challenge looks like, there's a PDF file attached to it.
Lets start by opening up the PDF file. We were greeted by this.
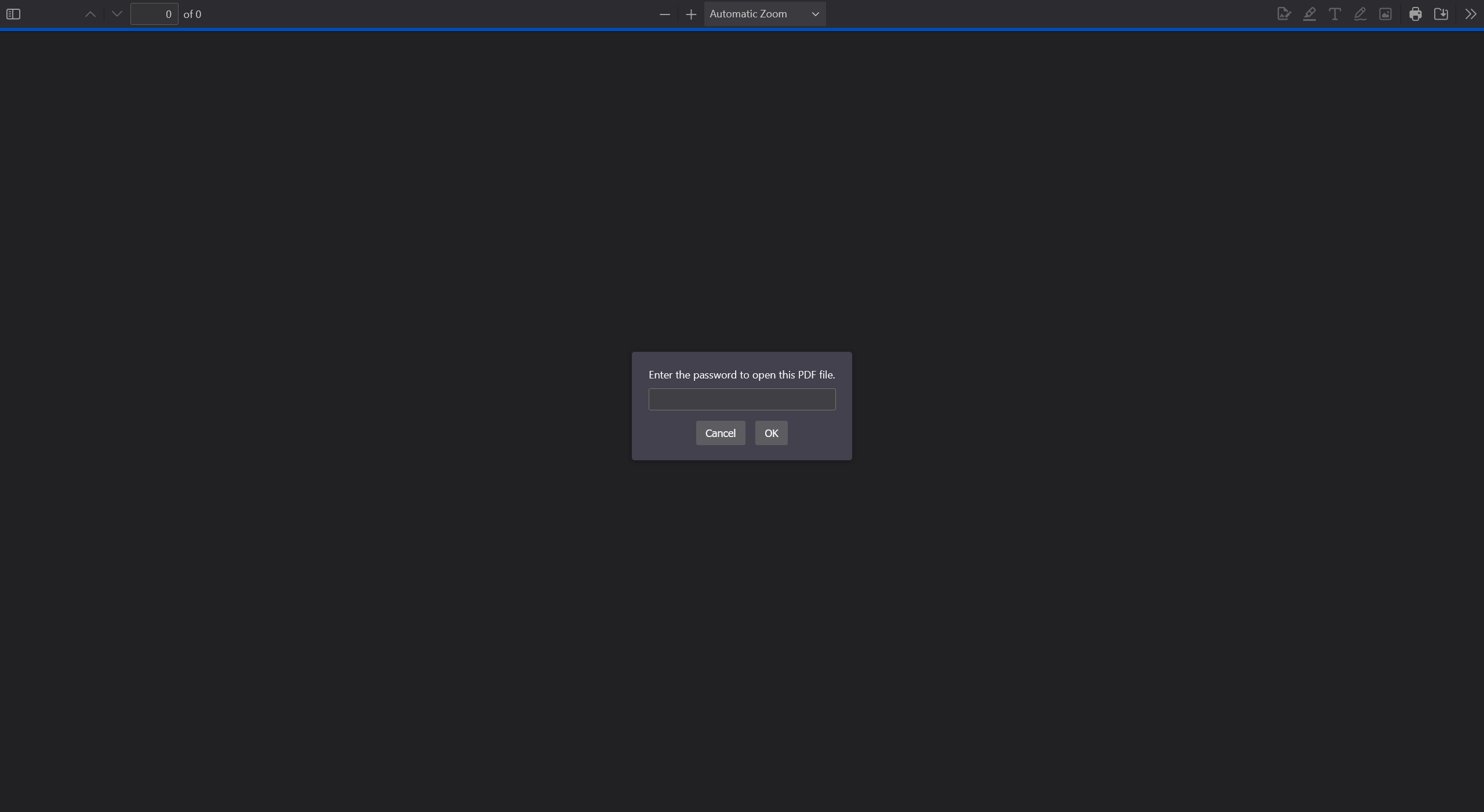
Looks like the PDF is locked, lets try to crack it now! We start by extracting the PDF password hash using pdf2john. And we can crack it using john.
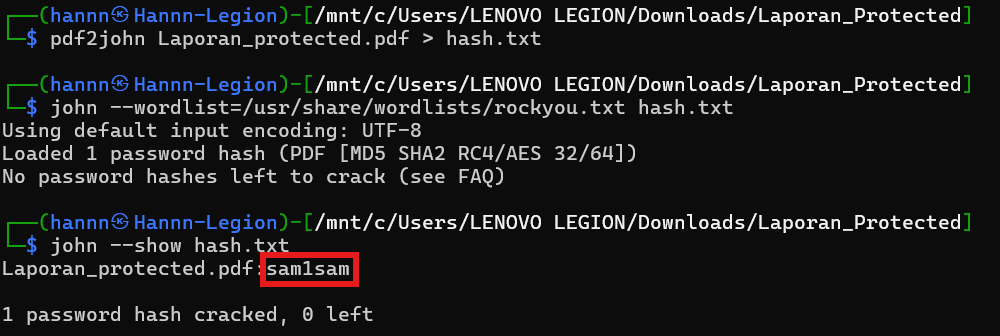
Great! The passworod is sam1sam, next, lets try to open the PDF again. This is what will greet you when you open the PDF.
It looks like that there's a JS file called pdf.js inside the PDF. Lets extract it. First, we need to extract the decrypted PDF. We can do it using qpdf
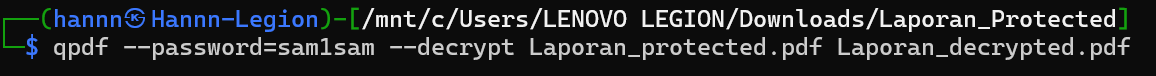
Next, we can use pdf-parser to extract the javascript. The pdf-parser outputs a bunch of streams, but we can find the stream containing the JS easily.
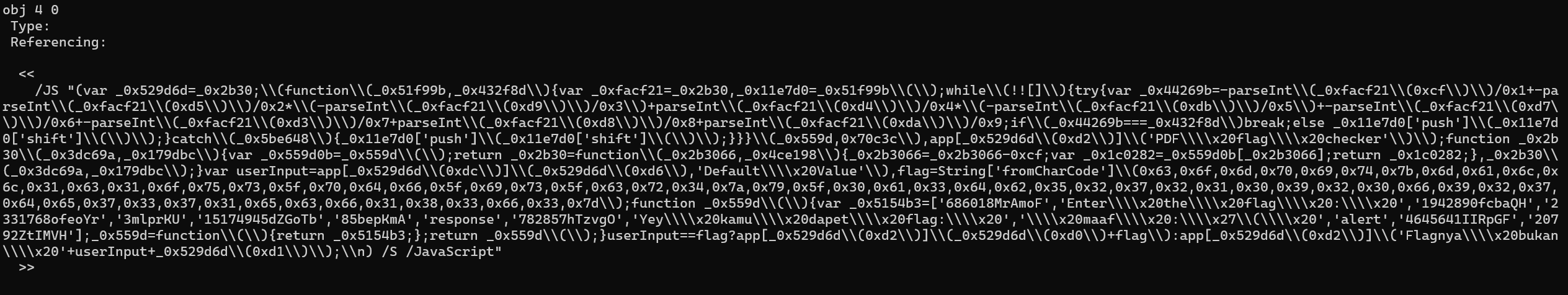
Next, lets enslave an LLM to help us extract the clean JS and deobfuscate it. It outputs us this cleaned up code.
// Prompt the user
var userInput = app.response("Enter the flag :", "Default Value");
// The actual expected flag is literally hard-coded:
var flag = String.fromCharCode(
0x63,0x6f,0x6d,0x70,0x69,0x74,0x7b,
0x6d,0x61,0x6c,0x6c,0x31,0x63,0x31,0x6f,0x75,0x73,0x5f,
0x70,0x64,0x66,0x5f,0x69,0x73,0x5f,
0x63,0x72,0x34,0x7a,0x79,0x5f,
0x30,0x61,0x33,0x64,0x62,0x35,0x32,0x37,0x32,0x31,
0x30,0x39,0x32,0x30,0x66,0x39,0x32,0x37,0x64,0x65,
0x37,0x33,0x37,0x31,0x65,0x63,0x66,0x31,0x38,0x33,0x66,0x33,0x7d
);
// Show success or failure
if (userInput == flag) {
app.alert("Yey kamu dapet flag: " + flag);
} else {
app.alert("Flagnya bukan " + userInput + " :(");
}
And evaluating the flag will give us...
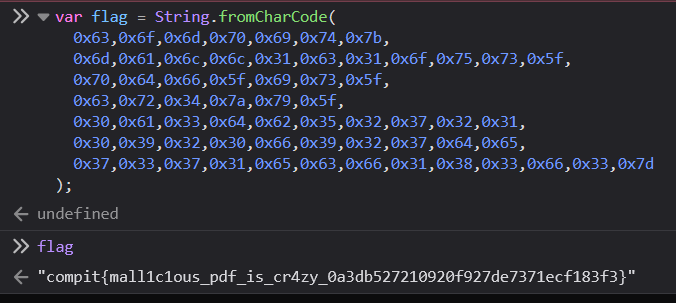
PO- PO- PO- PWNED!!!