antidebug-me
Solved by: grb
This is what the challenge looks like, there's a binary file attached with it. There's something special about the binary... ITS FINALLY A WIN32 PE BINARY!!! Finally, a change.
As usual, lets open the binary under IDA. This is the function that will greet us.
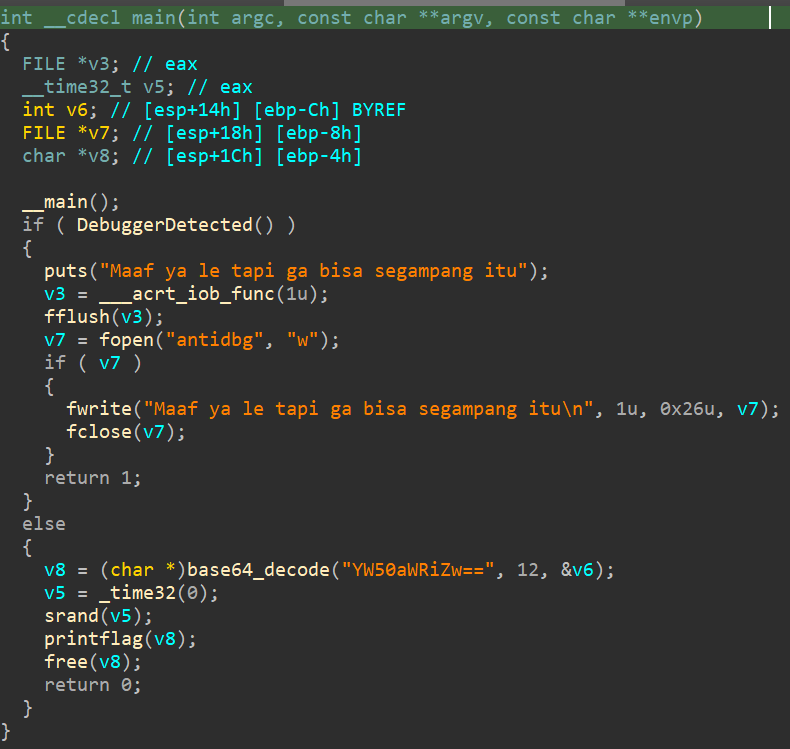
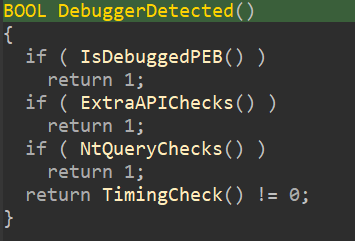
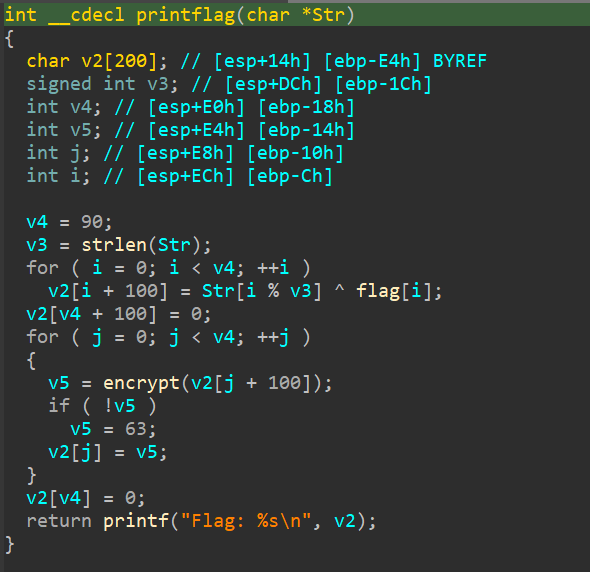
So, the main function checks if there's signatures or signs or clues of debugger running. If there isn't, the code is trying to catch us lacking by adding the time32 and srand function call, it tries to make us thinking "Oh shit there's some kind of runtime environment encryption or some shit, we must solve this dynamically!", but nuh uh, I aint that stupid bruh. We dont need any debugger to solve this challenge. Let's clean up the printflag function and check it out.
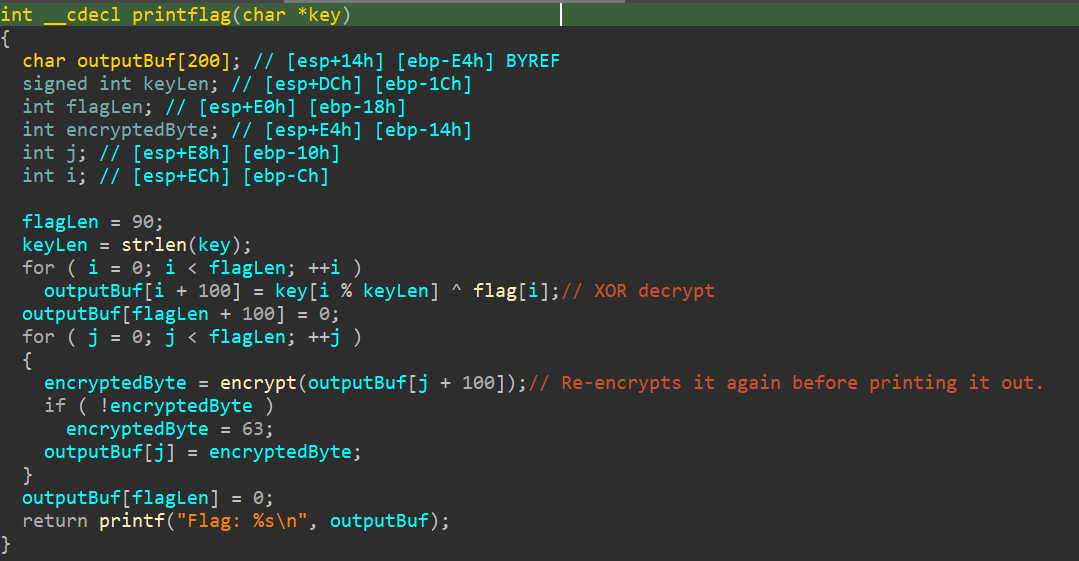
So as you can see, it is so obvious that the flag can be easily XOR decrypted manually. The XOR key itself can easily found in the main function, encoded in base64. Lets use cyberchef to decrypt it!
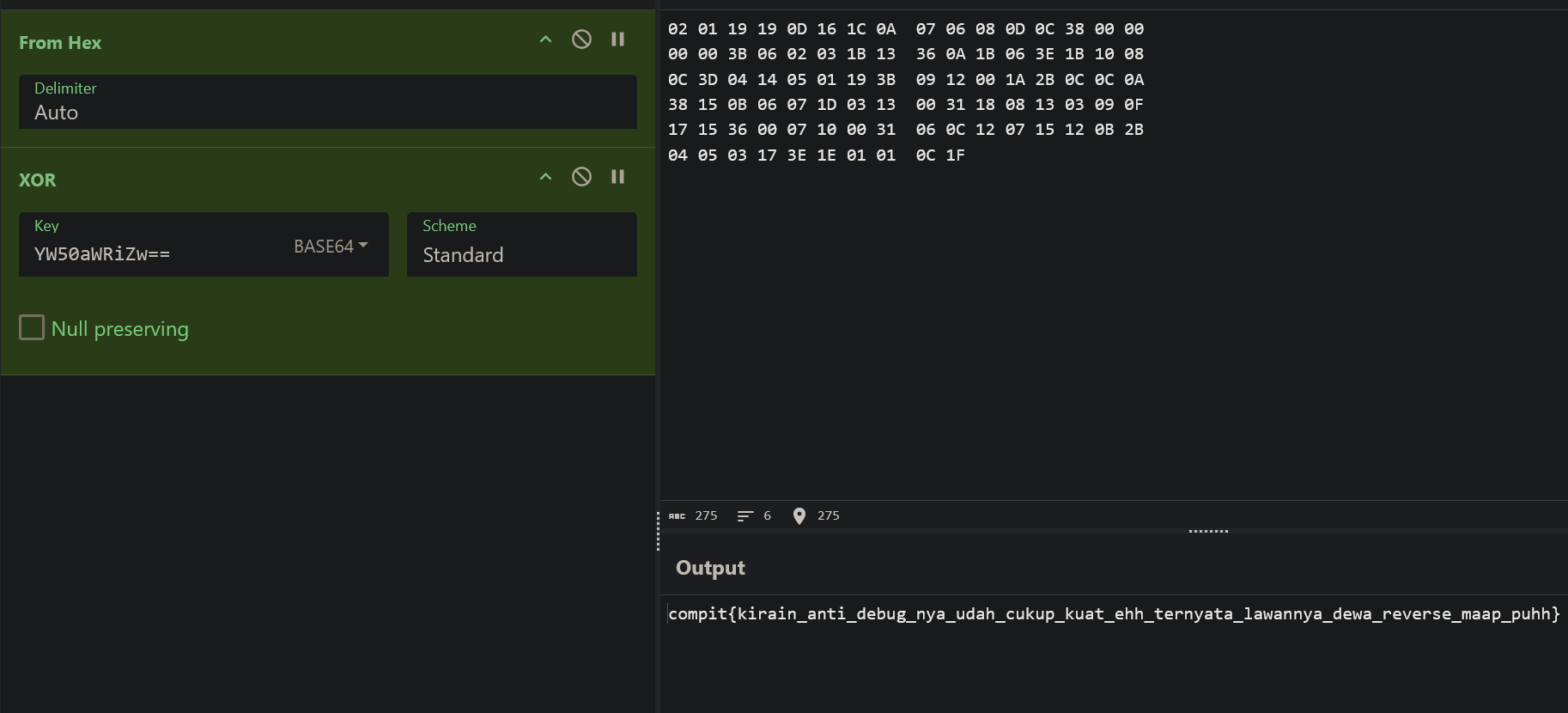
PO- PO- PO- PWNED!!!