capture-me
Solved by: grb
This is what the challenge looks like, there's a binary file attached with it, and its a Windows PE binary!
Just like our routine, lets check out the binary under IDA.
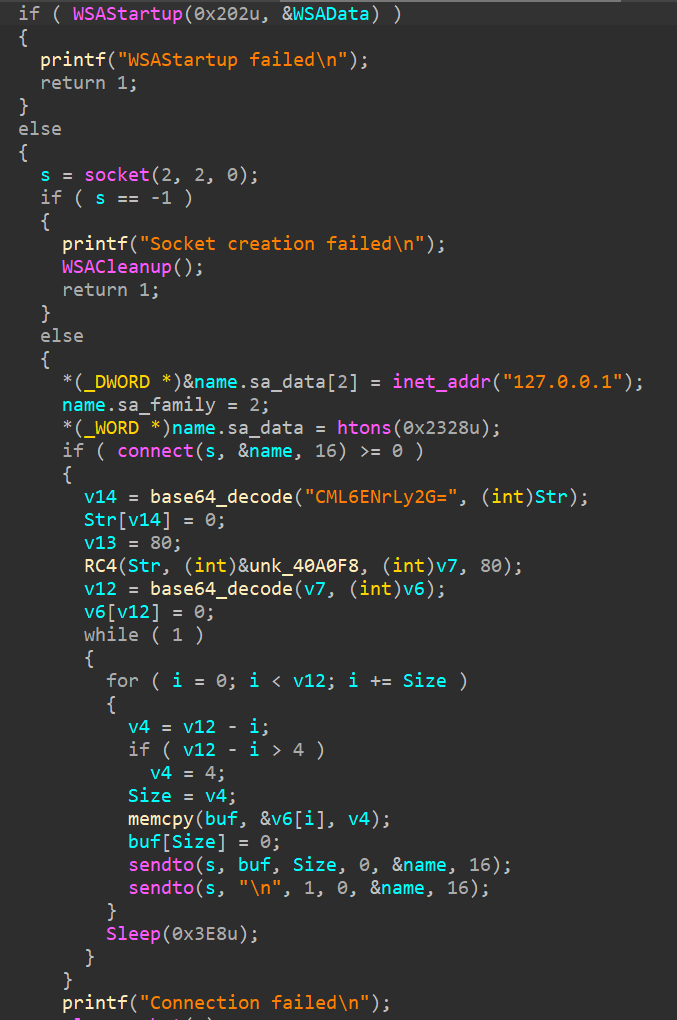
This is what the core of main function looks like, sorry because I cant find the whole function. Anyway, we can see that it tries to connect to localhost and send some data to it. Because its 11pm when I solved this challenge, I already got tired asf so lets do this the easy way. We will hook into the sendto API/function and peek into the data that it tries to send. Let's use API Monitor.
This is what it looks like on the first time you open it up.
On the left side of the window, you can find the "API Filter" tab
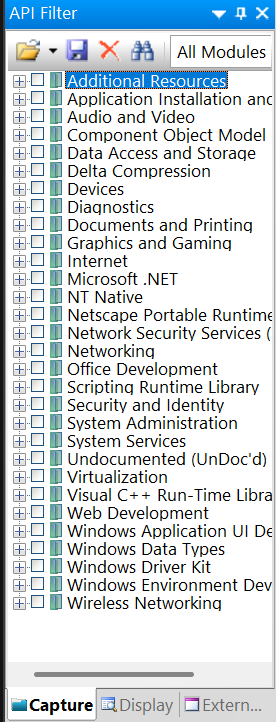
On the "API Filter" tab, you can click the binoculars logo and search the api sendto
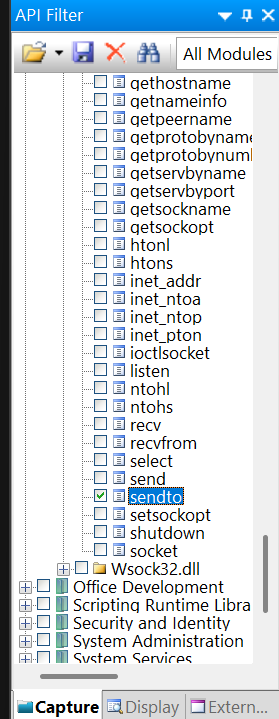
And when you find it, click it.
After that, go to the "Monitored Processes" tab and pick our target binary.
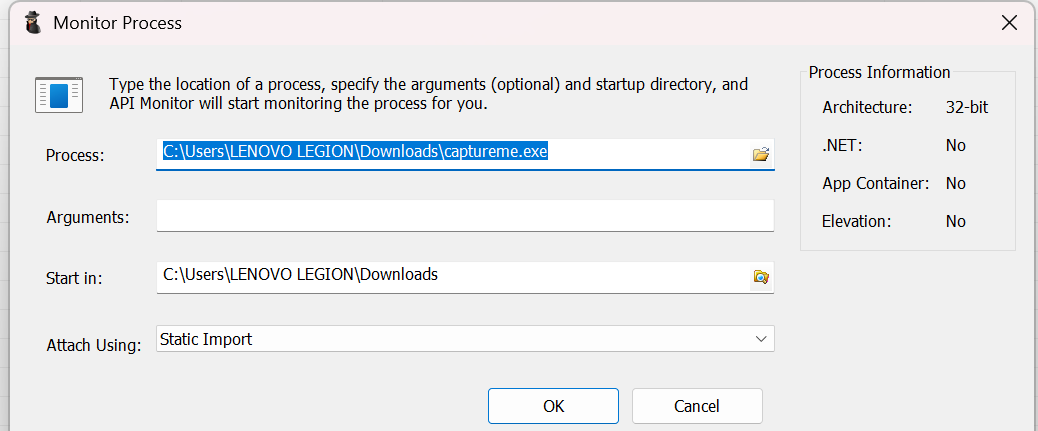
After you click "ok", you can already smell of the flag flowing...
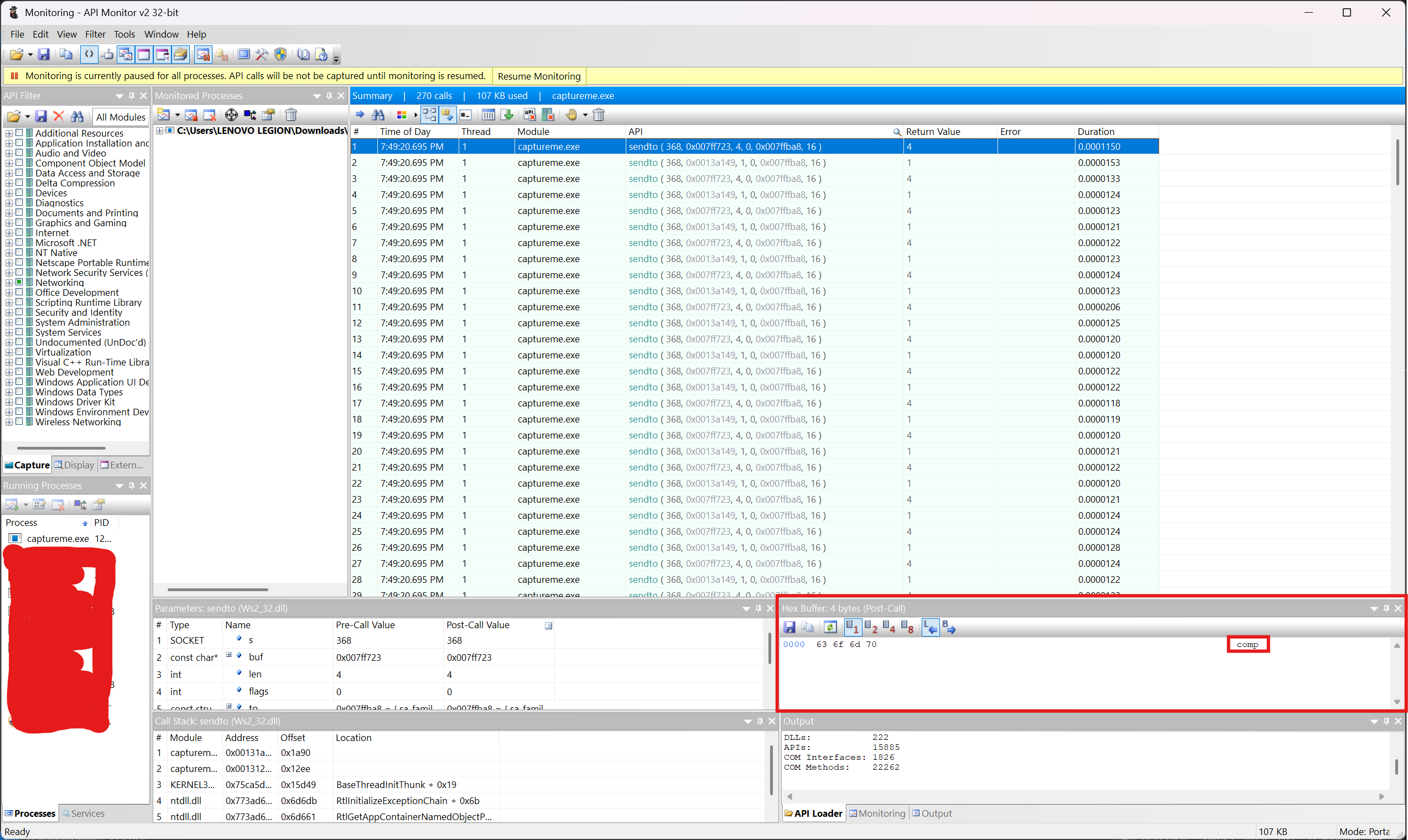
Just go through the captured sendto calls and combine the flag string.
Flag : compit{jangan_tangkap_flag_doang_tapi_tangkap_juga_paketnya}
PO- PO- PO- PWNED!!!