debug-me
Solved by: grb
This is what the challenge looks like, as usual there's a binary file attached with it.
And as always, lets check out the binary under IDA.
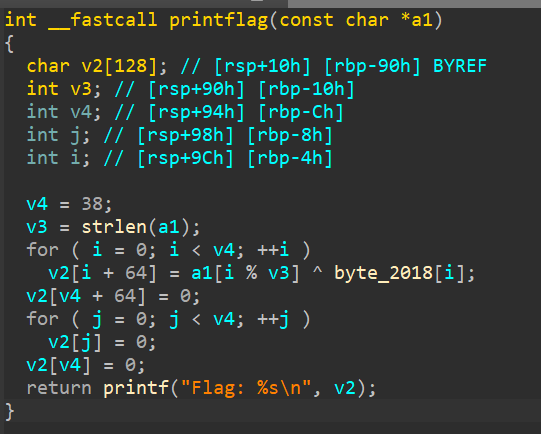
So, as you can see from the decompilation, the main function calls the printflag function with the string "debugger" as the parameter, and in the printflag function, we can see that that string is used to XOR decrypt a piece of data. There's 3 way to approach this, we can feed this decompilation and the data to your favorite LLM, we can play by the book and use a debugger, or we can manually decrypt the data.
Lets play by the book and use a debugger! But before that, lets analyze a bit deeper on the printflag function.
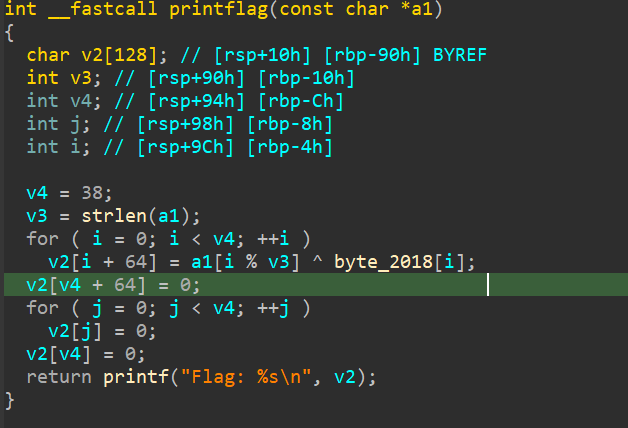
You can see in this part that the function decrypts the data correctly, but then...
They null the whole buffer and print it, which means when we run the program, we just get a whole lotta nothing. Thats why when we use the debugger, we need to put a breakpoint on a specific instruction right before it nulls the buffer. How can we pin point it? Here's how. First, you synchronize your IDA pseudocode with IDA-View and Hex-View

And then, you click the line where you want to put a breakpoint.
And switch to your IDA-View to get the function offset of that line.
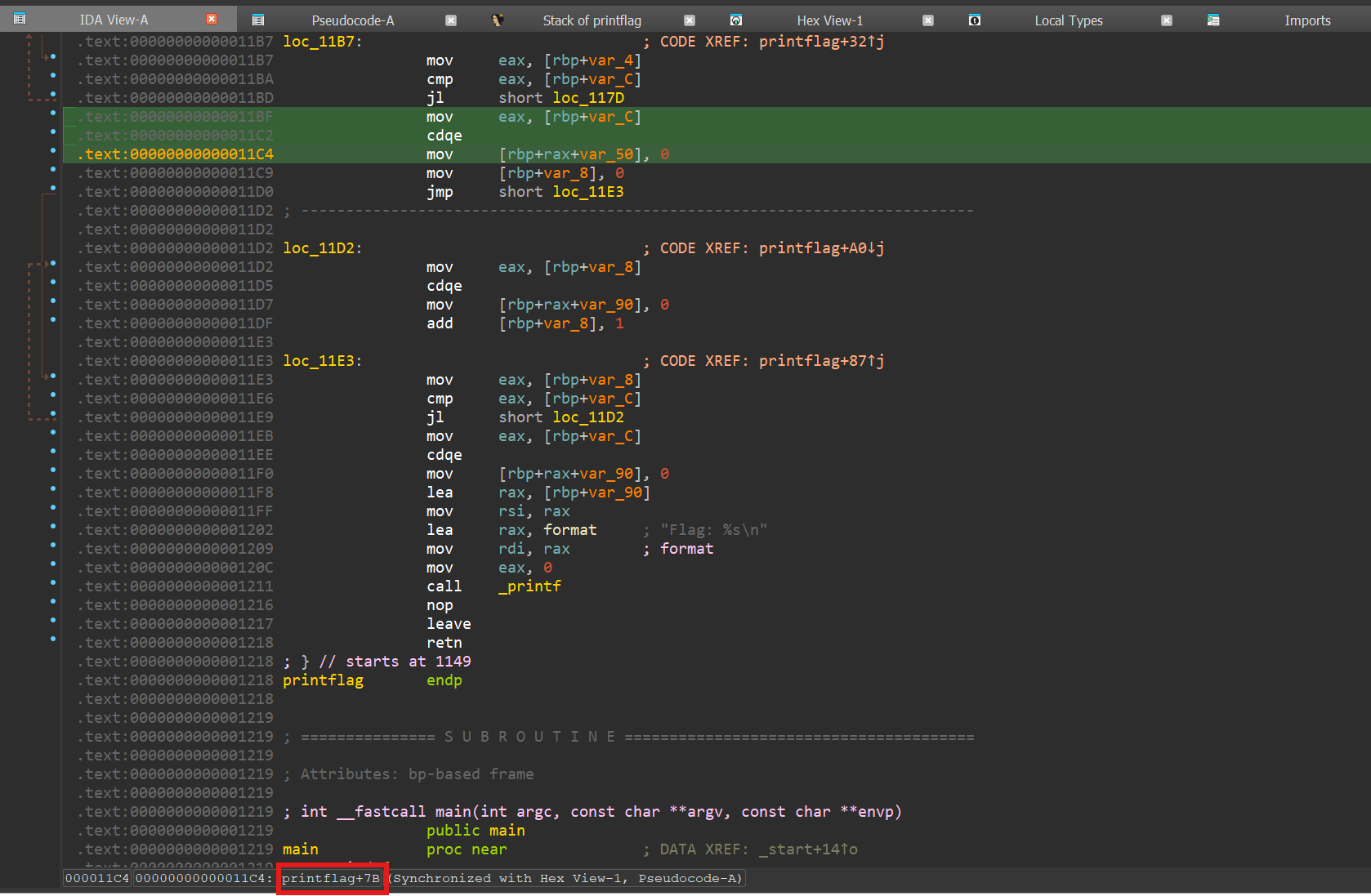
Next, this is how you debug and and set our breakpoint to our target.
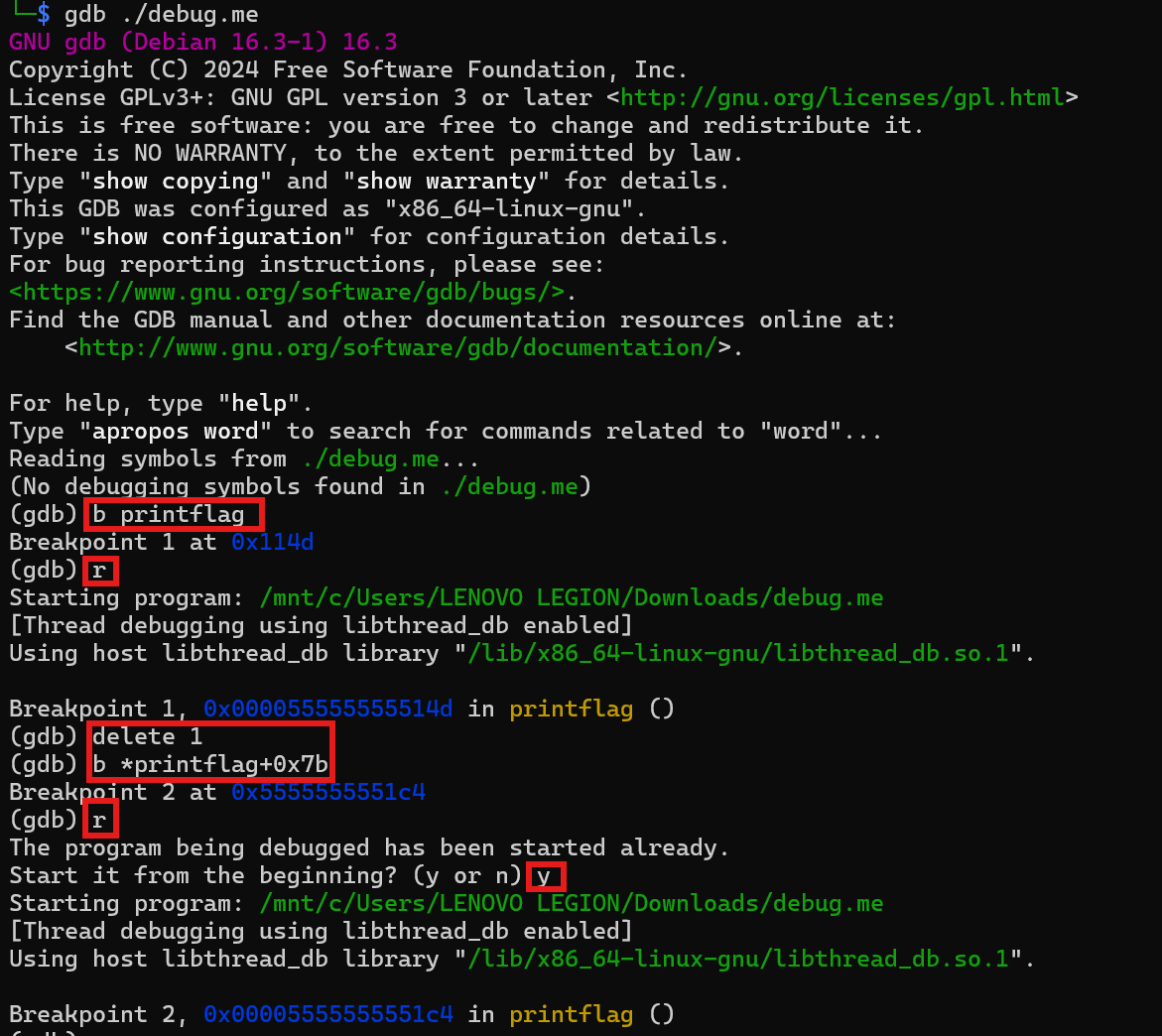
And when our breakpoint is hit, we can just dump the stack with the command x/100s $sp and get our flag.
PO- PO- PO- PWNED!!!