keygen-me
Solved by: grb
This is what the challenge looks like, there's a python script attached with it.
This is what the python script looks like.
SECRET_KEY = "F2AC-58FD-9547-988E-46E5-9D25-EEBC-3AD5-BF51-E4B4"
def pad_inputs(username: str, password: str):
u = (username[:12]).ljust(12, "_")
p = (password[:8]).ljust(8, "0")
return (u + p).encode("utf-8")
def rotl8(x, n):
return ((x << n) & 0xFF) | (x >> (8 - n))
def make_key(username: str, password: str) -> str:
data = pad_inputs(username, password)
mask = [0x13, 0x37, 0x42, 0x99, 0xAB, 0xCD]
transformed = bytes([
rotl8(b ^ mask[i % len(mask)], 1)
for i, b in enumerate(data)
])
hexed = transformed.hex().upper()
return "-".join([hexed[i:i+4] for i in range(0, len(hexed), 4)])
def main():
print("Welcome to CompitKey v1.0")
guess_user = input("username: ").strip()
guess_pass = input("password: ").strip()
if make_key(guess_user, guess_pass) == SECRET_KEY:
print("Correct! Flag: compit{" + guess_user + guess_pass + "}")
else:
print("Nope")
if __name__ == "__main__":
main()
Basically, this code validates username and password input by generating a key and comparing it with the stored key SECRET_KEY.
To be frank with yall, I enslaved an LLM to make me the decryptor script, and this is what it generates.
# invert_compitkey.py
SECRET_KEY = "F2AC-58FD-9547-988E-46E5-9D25-EEBC-3AD5-BF51-E4B4"
mask = [0x13, 0x37, 0x42, 0x99, 0xAB, 0xCD]
def rotr8(x, n):
return ((x >> n) | ((x << (8 - n)) & 0xFF)) & 0xFF
hexed = "".join(SECRET_KEY.split("-"))
tbytes = bytes.fromhex(hexed) # 20 bytes (12 + 8)
orig = []
for i, b in enumerate(tbytes):
orig_byte = rotr8(b, 1) ^ mask[i % len(mask)]
orig.append(orig_byte)
orig_bytes = bytes(orig) # combined padded username+password
username = orig_bytes[:12].decode('utf-8')
password = orig_bytes[12:].decode('utf-8')
print("flag: compit{" + username + password + "}")
And running the script will get us...
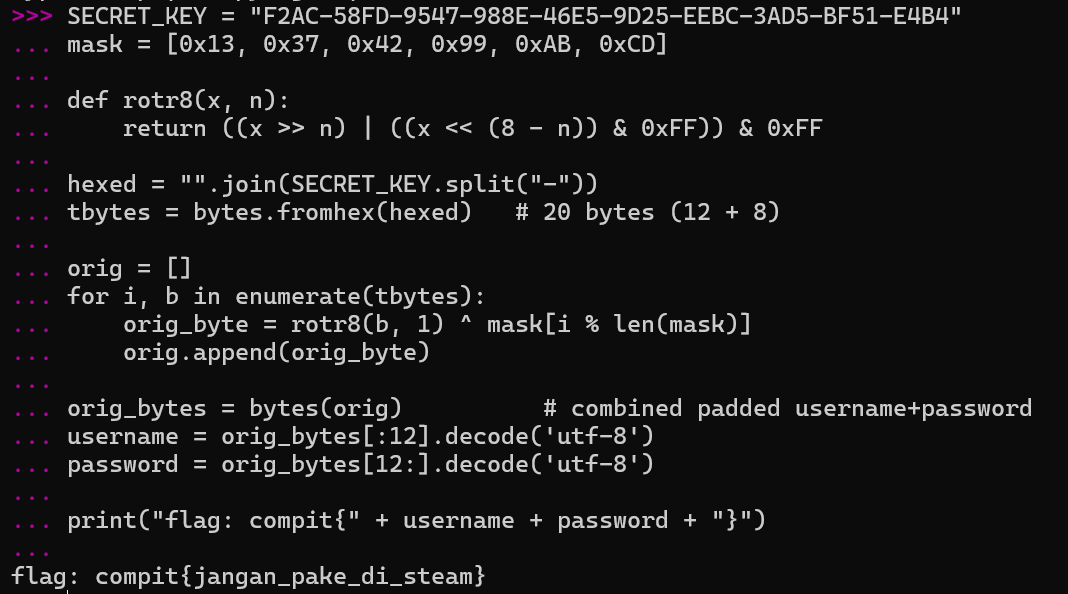
PO- PO- PO- PWNED!!! Not so proud of this one but meh, I dont like crypto shit anyway.