patch-me
Solved by: grb
This is what the challenge looks like, there's a binary file attached with it.
As always, lets open up the binary under IDA.
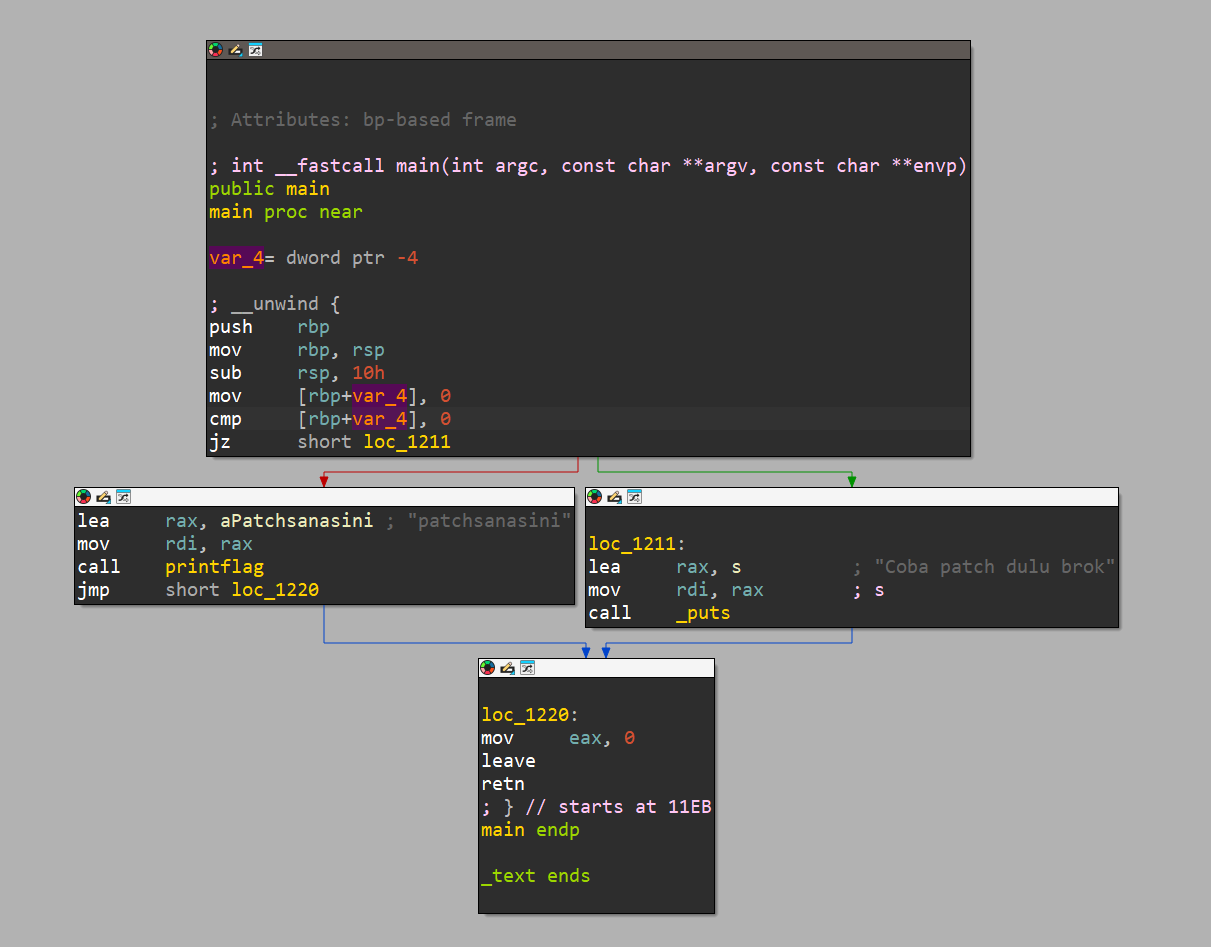
As you can see here, the original disassembly and the pseudocode generated by IDA is different. This is because IDA detected a code flow that would never be executed, and it didnt generate a pseudocode for it. So, for this challenge lets focus on the disassembly a bit.
As you can see from the image above, it sets a variable in the stack to 0, and then compare if it 0. This is what I meant from before, a code flow that would never be executed because the output from the comparison would always be the same. And because the cmp instruction returns an equal, the ZF flag is set and the jump by jz instruction will be executed. It will jump to here
Prints "Coba patch dulu brok" and exits, but we know that there's a hidden code flow, which is this one.
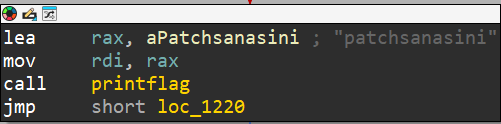
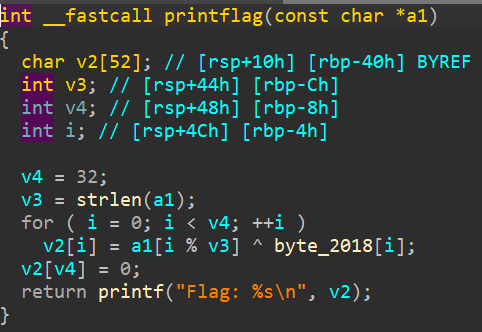
There's 2 way to approach this challenge, either you play by the book and patch the instruction where it sets a variable in the stack to 0, or you could do a static analysis of printflag function and decrypt the data ourself. This is what the printflag function looks like
For now, lets play by the book and patch the instruction! First, lets check the instruction that sets the variable in the stack to 0.
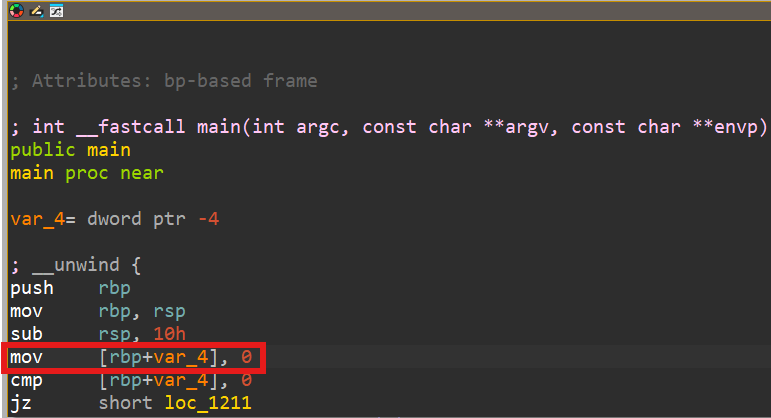
Next, lets check the bytes of this instruction, but before that, you need to synchronize your IDA-View to the Hex-View.
Next, pick our target instruction and check the Hex-View.
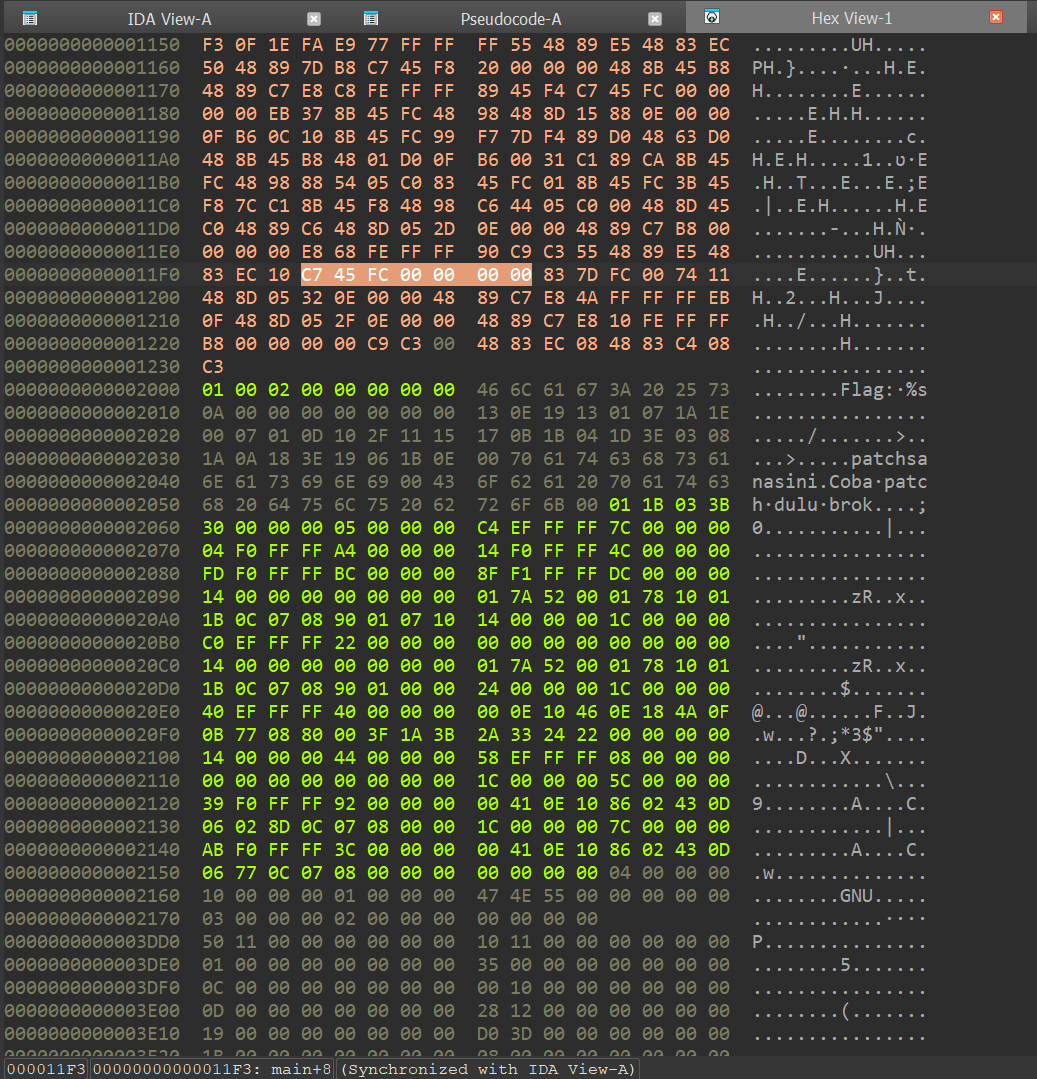
So, our instruction's bytes is C7 45 FC 00 00 00 00. The one that we need to modify is the last 4 digit, which is the operand of the mov instruction. Next, we can use any of your favorite hex editor to patch the binary, I personally use HxD. Next, find the bytes of the instruction.
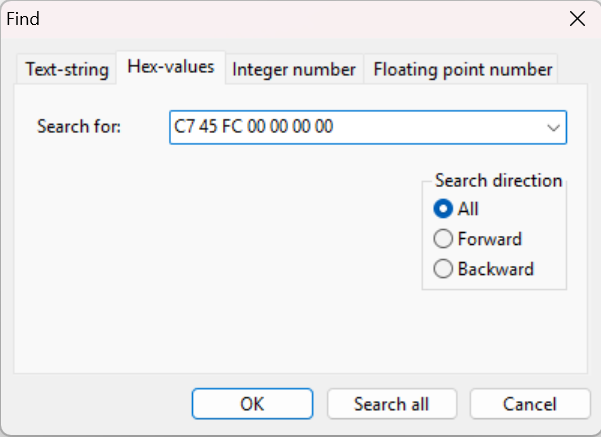
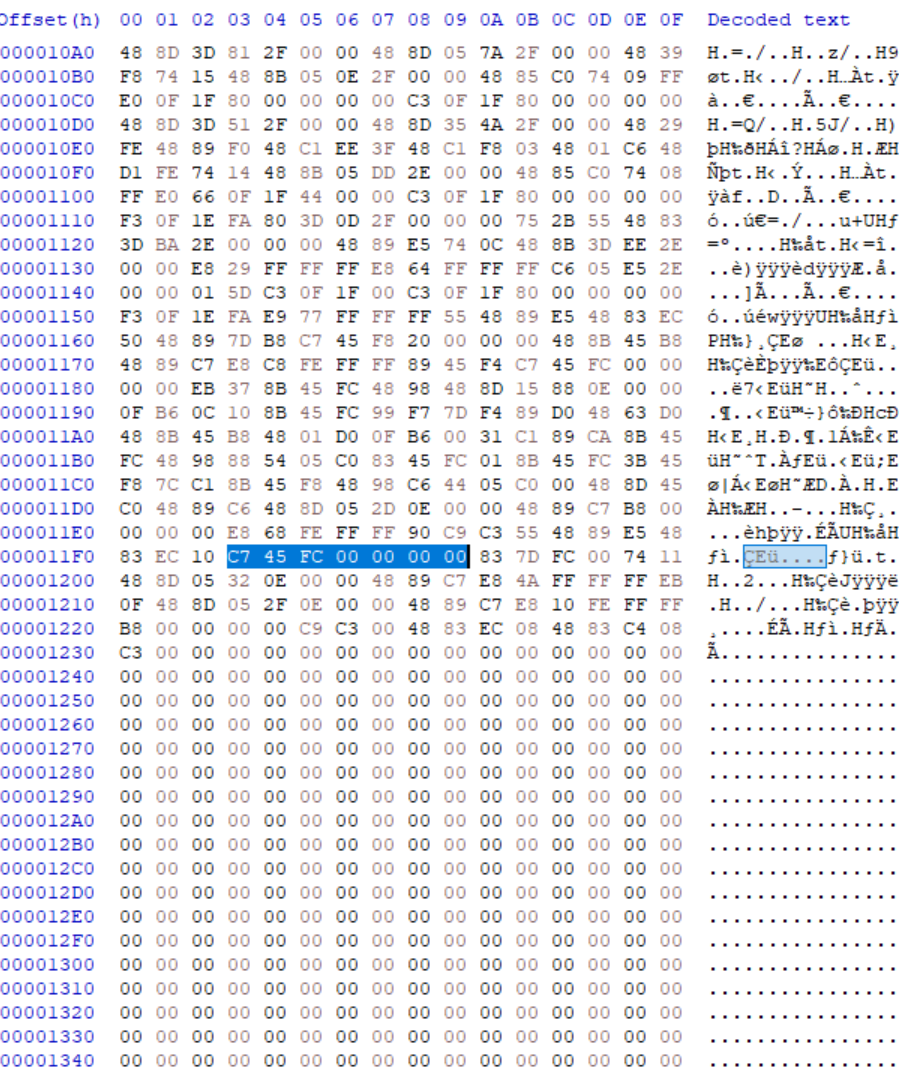
Now, patch one of the bytes, here, I changed the instruction bytes to C7 45 FC 01 00 00 00. Saved it. And when we run the binary again...
PO- PO- PO- PWNED!!!