Lock Picking
Solved by: Hanxoe
I just made a vault to store my treasured things, it should be very secure right?
10.4.79.68:20004
author: anarchistx
Alright, it's time for the Lock Picking challenge. We were immediately greeted by a login form when accessing the URL.
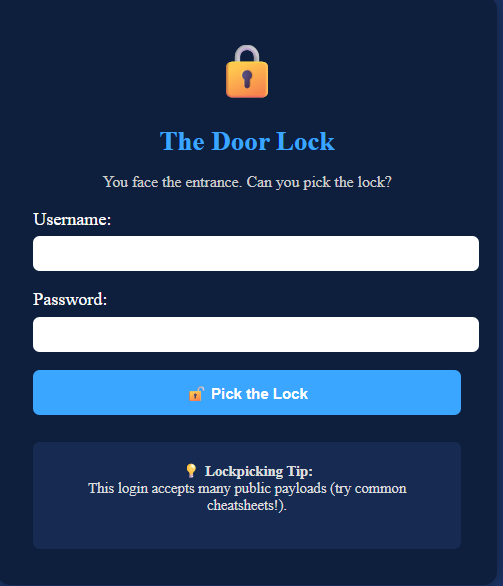
Okay, we're going to try a very common vulnerability in forms: SQL injection. Let's start with a simple payload like ' or 1=1 --
Andddddd yepppp, we've hit the second form🙃😭
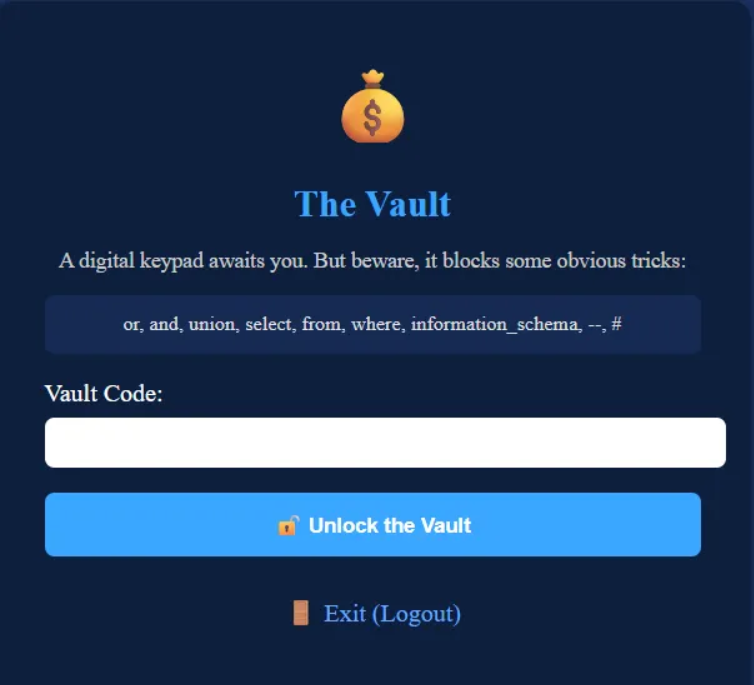

We'll be utilizing a potent SQL payload known to bypass common string filters:
' || CHAR(79)||CHAR(82)||CHAR(49)||CHAR(61)||CHAR(49) ||CHAR(45)||CHAR(45)||'.
This sequence is the character-encoded form of the classic ' or 1=1 -- injection. It's crucial to remember that this technique is primarily effective on specific databases such as PostgreSQL, Oracle Database, and SQLite. We must also ensure we include single quotes at the beginning and end to properly concatenate (or 'balance') the payload with the surrounding query, preventing syntax errors.
And the result is...
compit{d1d_y0u_just_unl0ck_th1s_v4ult?_c0ngr4tz_th3n_y0u_th13f}